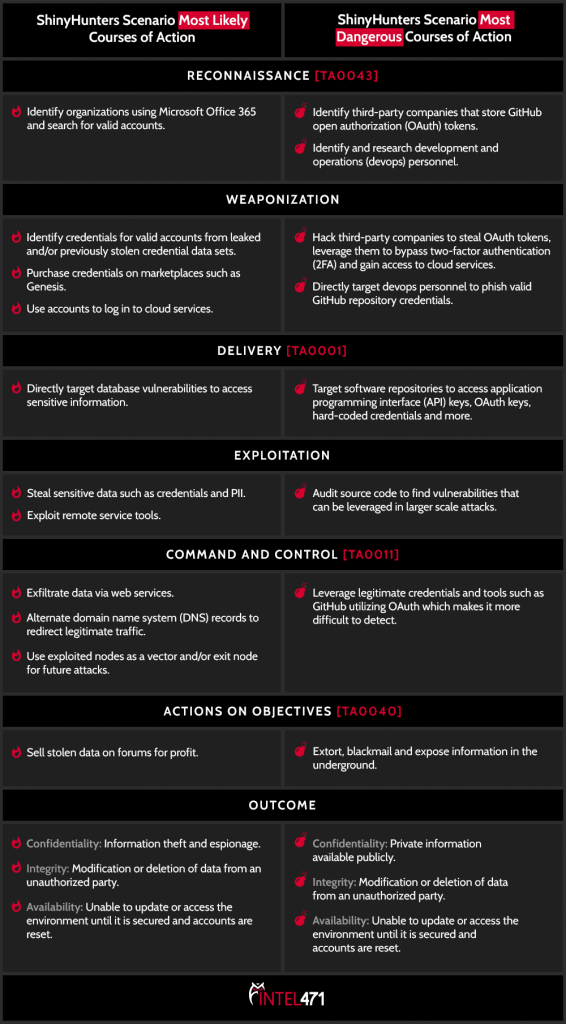
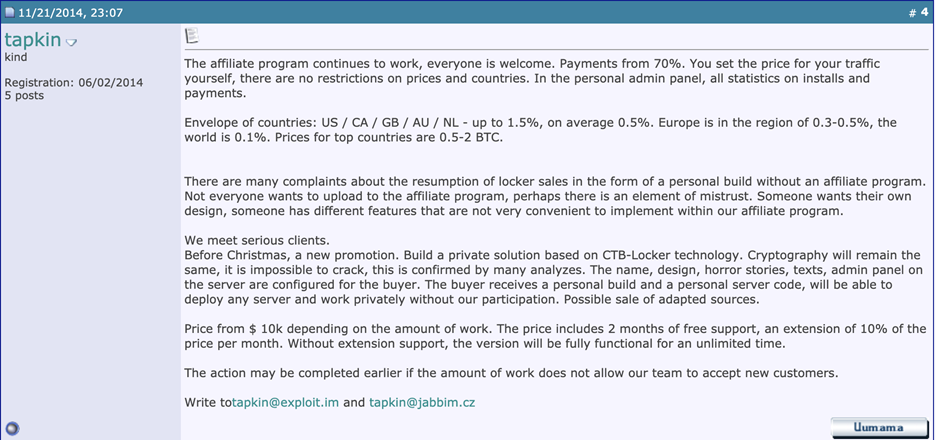
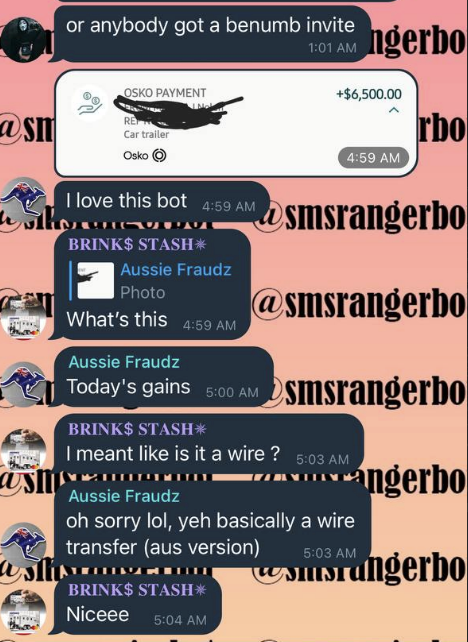
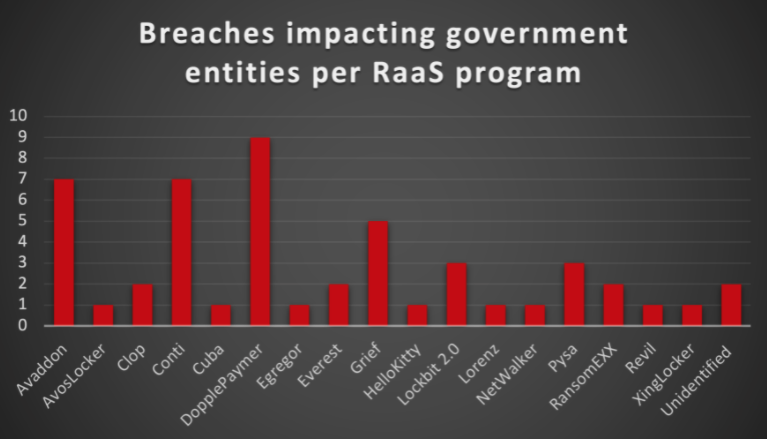
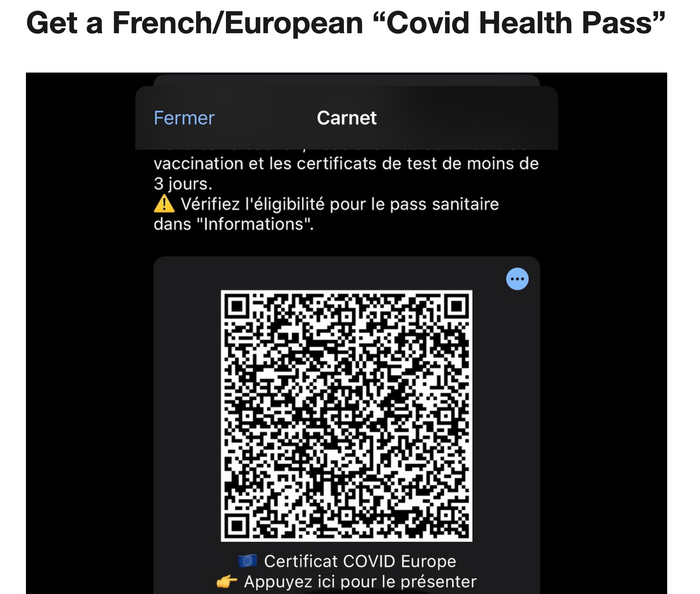
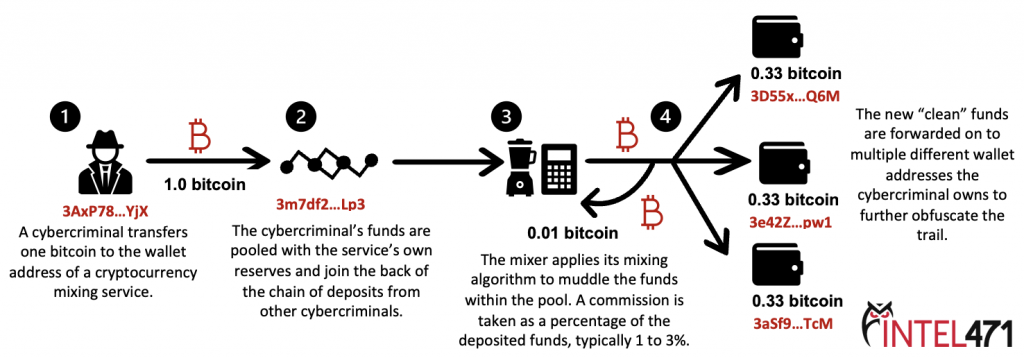
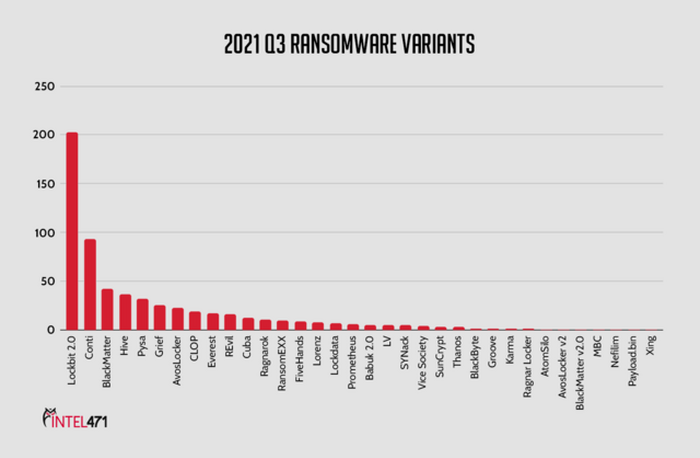
Cybercriminals have so many schemes aimed at your…
Be it personal or professional, it’s now an ordinary fact of life that people own dozens of different online accounts. From the essential to the mundane, every facet of our lives can be linked to a service that’s probably tethered to its users by an account name and password. For cybercriminals, those account names and …
Cybercriminals have so many schemes aimed at your… Read More »