Prioritizing “critical” vulnerabilities: A threat…
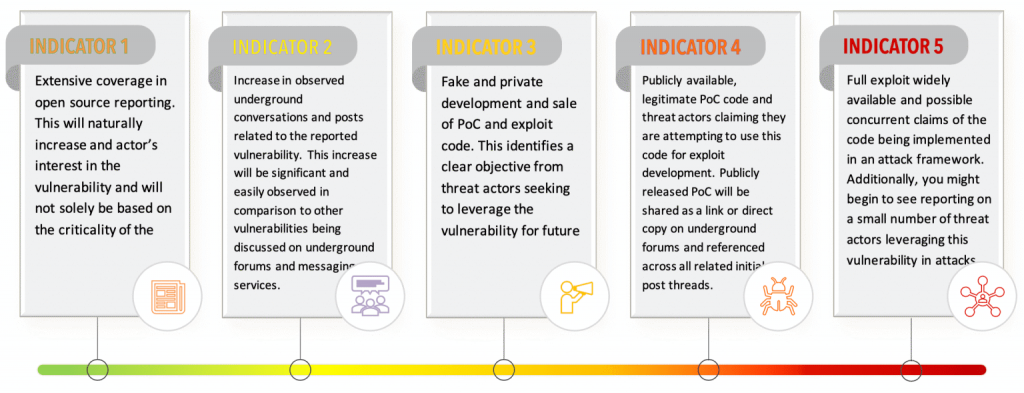
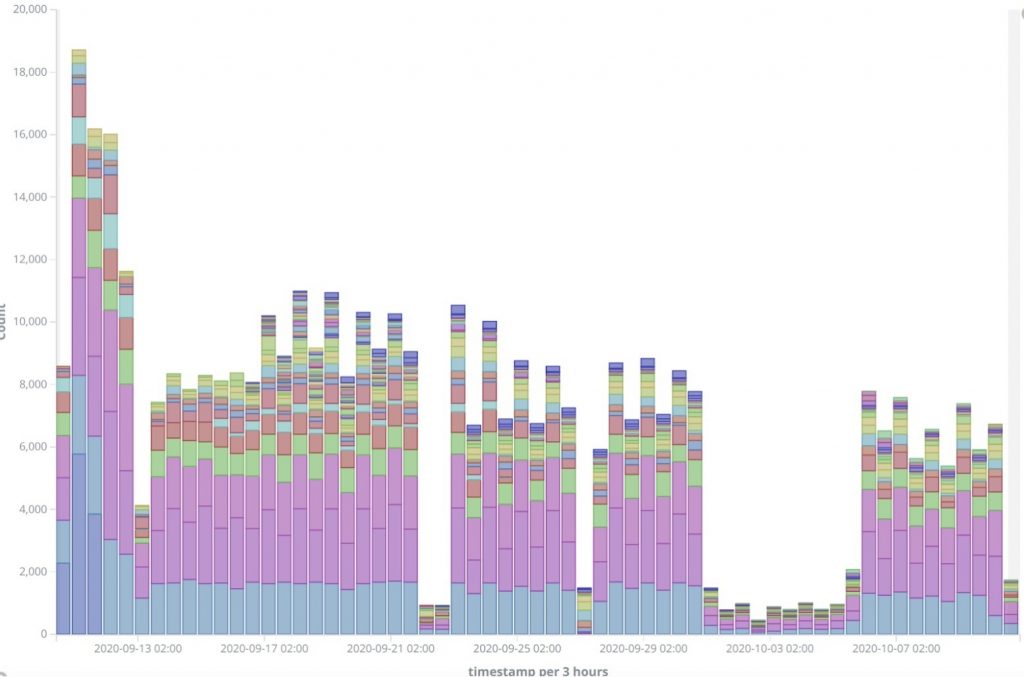
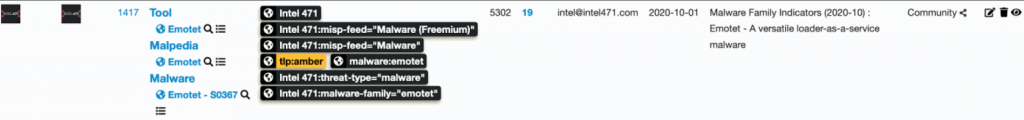
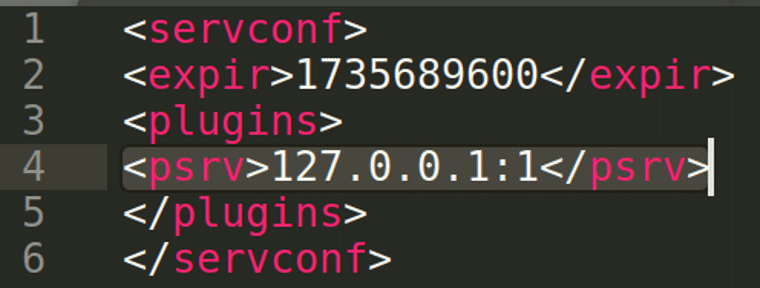
By the Intel 471 Intelligence Analysis team. Recently, there have been many vendor security advisories containing multiple critical vulnerabilities potentially impacting organizations that may be conflicted with patch prioritization when looking at the variables seen for each reported vulnerability. Threat intelligence can supplement publicly disclosed information and provide a contextual view of exploitation efforts and …
Prioritizing “critical” vulnerabilities: A threat… Read More »