A June 2020 feature in The New Yorker was really more cyberpunk than cybersecurity. The story focuses on the people who ran CyberBunker, a server farm built in an underground European military bunker that served as a host for spammers, botnet command-and-control servers, malware and online scams. The story follows the familiar arc of dystopian techno-fiction: an absolutist attitude toward privacy, the use of technology to commit crimes, and the eventual downfall in the form of law enforcement action.
While the CyberBunker story is a dramatic one, it was a very real example of how Bulletproof Hosting (BPH) is the foundation for so much of the cybercrime we see today. While even those with a cursory knowledge of BPH can conjure up images of server racks hidden in far-flung corners of the world, the reality is that BPH services often take place on machines and services hiding in the everyday noise of the internet.
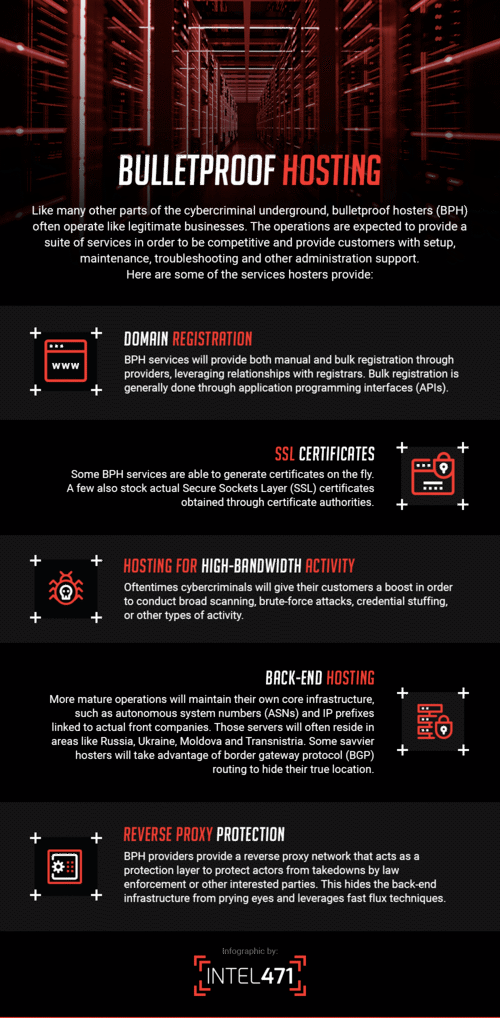
The following entry will define what a typical BPH service offers and how these services can be stopped in order to limit the damage they have on enterprises, businesses and digital society itself.
The Power of Fast Flux
WHAT IS IT: Fast flux is a DNS technique where IP addresses tied to a particular domain are quickly changed or swapped out in an effort to hide malicious activity from defensive measures.
Once in use, the domain names tied to the quick-changing IP addresses serve as a proxy to carry out all sorts of cybercriminal activity. There are three types of Fast Flux models:
Bot-based models, where malware infected machines are used as proxies. A website’s A-records (which point to host names, such as www, ftp, mail) will basically reflect the IPs of these particular bots. There’s another more resilient model, known as Double Flux where both A-records and NS-records (which specify the servers which are providing DNS services for a certain address) point to infected machines/bots.
Another model is based on a handful of virtual private servers purchased by bad actors that mimic legitimate traffic in order to avoid detection. When used, actors will rely on a DNS provider like DNSPOD to manage the changing of A-records for the handful of IPs/VPSs that your domain will use. For extra money, bulletproof hosters will also set up dedicated nameservers for you as well.
The third model is when an actor has a pool of cloud instances that all of his clients will share over time. Each client will use a specific IP at any given time, but over time it will bounce around to various clients. Depending on the provider, a specific host could live for a few hours or a few months.
WHY THIS IS SO HARD TO STOP: The list of IP addresses used by these actors can stretch into the hundreds of thousands. When in use, they are attached to a DNS record for an average of five minutes, then swapped out for a different IP address, all in the name of avoiding detection. If it were possible to track in real-time, it would be akin to searching for needles in a haystack, only the needles are moving to different haystacks before any human or machine has a chance to react.
Another reason these services are hard to track is actors’ use of legitimate cloud service providers. When hosters leverage legitimate cloud providers as front end proxies, it blends in with other legitimate-looking traffic, making it extremely difficult for defenders to differentiate between good and bad traffic.
HOW CAN THIS BE STOPPED: Due to the speed by which this technique is used, it’s nearly impossible to catch actors in real-time. However, behaviors such as bulk procurement of domain names, clearly faked registration information for nameservers, and rapidly alternating IP addresses from those domains are red flags for malicious behavior. It is upon multiple organizations — internet registrars, ISPs, cloud service providers — to work together to ultimately detect this behavior before actors develop infrastructure that takes further advantage of legitimate platforms.
The Hardware is Somewhere
WHAT IS IT: BPH via data centers — Think back to CyberBunker — are hosting services that own and maintain their own hardware, but go to great lengths to conceal their customers’ identity, where they are located, and prevent law enforcement from shutting them down. Services can be provided that ultimately use hardware from a compromised service provider, or an outfit that bribes officials or police to look the other way. These organizations are often located in areas where law enforcement is known for its corruption or lackadaisical approach to enforcing the law: Ukraine, Seychelles, and Belize are home to some of the most popular BPH data centers in the world.
WHY THIS IS SO HARD TO STOP: The way these data centers are stood up is done by design: Geographic locations are often picked to fit where shady customers are looking for such services, local laws are easier to comply with or skate around, and protection from domestic law enforcement is available either wittingly (most likely through a bribe) or unwittingly through government negligence, lack of legal support or resources to enforce the laws needed to take down infrastructure and hold operators accountable.
HOW CAN THIS BE STOPPED: International law enforcement partnerships, along with help from private sector cybersecurity companies, have started to make a dent in the number of bulletproof hosting services available to cybercriminals. A good example of this is the recent action led by Europol, which seized three prolific web domains — safe-inet.com, safe-inet.net and insorg.org — used to hide the activities of ransomware gangs and other illegal operations. There has been an uptick in similar actions over the past few years, showing that human intervention is the best way to combat the criminals behind these services.
As much as the people behind these services try to hide their actions, there is only so much they can do to prevent detection. Bulletproof hosting providers operate a business for financial gain and need to advertise their offerings, and they cannot do that in silence. Therefore, while difficult, it is essential to establish ways to gather intelligence on these known services, so security practitioners can clearly understand how they operate and take steps to detect and mitigate attacks. Like we have said before, When we intimately understand criminals’ business models, processes, enablers and pain points, enterprises can find themselves ready to take action and proactively counter the threats they face.
This the first entry in a forthcoming three-part series.
Ten articles before and after
Egregor operation takes huge hit after police raids
Bulletproof hosting: How cybercrime stays resilient
Here’s who is powering the bulletproof hosting market
Friendly fire: Four well-known cybercriminal forums…
Cybercriminals still leveraging COVID-19 pandemic for…
Cybercriminals are interested in your SCADA systems
Emotet takedown is not like the Trickbot takedown
Last Dash for Joker’s Stash: Carding forum may close…