Intel 471’s Malware Intelligence provides our clients with constant coverage of top-tier malware families. It delivers near real-time alerts of targeting changes, spamming and malware campaigns, updates in infrastructure and much more. In the first in a series of blogs and white papers, we take a look at how this high-volume and high-fidelity data has been modeled in MISP and demonstrate how you can use the platform to make acquiring and processing the data more manageable.
What is MISP?
MISP is a free and open-source Threat Intelligence Platform (TIP) for gathering, sharing, storing and correlating indicators of compromise (IoCs) of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counterterrorism information. MISP allows you to store your data in a structured manner and thus facilitates correlation and automated exports for IDS/SIEM. A variety of formats are supported including STIX, STIX 2 and OpenIOC. Full details can be found at https://www.misp-project.org/.
Key Decisions
From the very outset of our decision to develop an integration with MISP, we had a few key goals in mind. First, we wanted to ensure our data was modeled in a way that provided maximum benefit and value for our customers. We didn’t want to simply push our data into MISP so we could “tick the box” and leave our customers to figure out how to process and further transmit the data. We spent a lot of time working with existing MISP users to understand how they use the platform and what we could do to make life as straightforward as possible for them. Decisions around how we should segment/slice data, how we should tag/classify intelligence and what the best mechanism would be to make our data consumable via MISP were all fundamental choices that would influence the usability of the integration.
Data Modeling
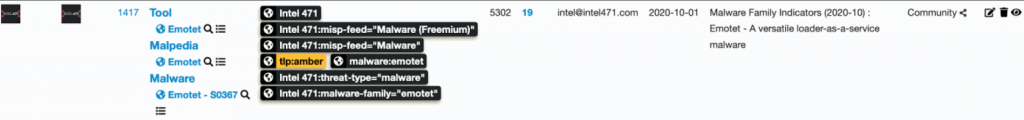
Intel 471’s Malware Intelligence currently covers more than 40 top-tier malware families. Our high-volume/high-fidelity data was an ideal candidate for inclusion in our first batch of MISP feeds. By taking advantage of MISP’s excellent Galaxies and Intel 471 custom tagging, we’ve delivered enhanced correlation capability without unmanageable complexity.
For each malware family we track, our MISP feed includes:
- A MISP Event containing the latest version of our in-depth technical report for the family.
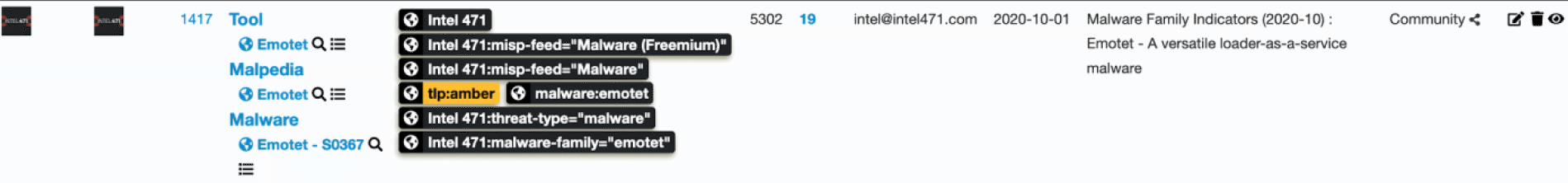
- A MISP Event containing attributes representing all indicators for which activity was observed during the referenced calendar month (e.g., Emotet 2020-10). First/last seen timestamps are updated throughout active months, in addition to indicator contexts and confidence levels as each indicator is continually probed and validated.
Comprehensive tagging is employed to deliver maximum context and insight for each indicator. However, care was taken to not “over tag,” which could have performance implications for MISP instances.
The time slicing of malware indicator data, with indicators neatly grouped by malware family per calendar month, also helps keep your MISP instance performant. Events with too many indicators, especially if attribute-level tagging is employed, can create issues for an under-resourced or inadequately tuned MISP installation. The time slicing also helps ensure you can identify and use the most relevant indicator data easily.
Beyond Simple Tags
All malware indicators included in our MISP feed are also tagged with references to our Cybercrime Underground General Intelligence Requirements (CU-GIRs). These help provide prioritized and focused context around all our data. They underpin everything we do and are used as our primary baseline tool to collect, classify and report frequently observed information found in the underground. Further insight into our CU-GIR framework can be found on our blog.
A Sample Use Case – Emotet
Emotet is a global threat that has been very active in recent years. The threat presented by Emotet has grown in the past year as some of the groups leveraging it for malware campaigns.
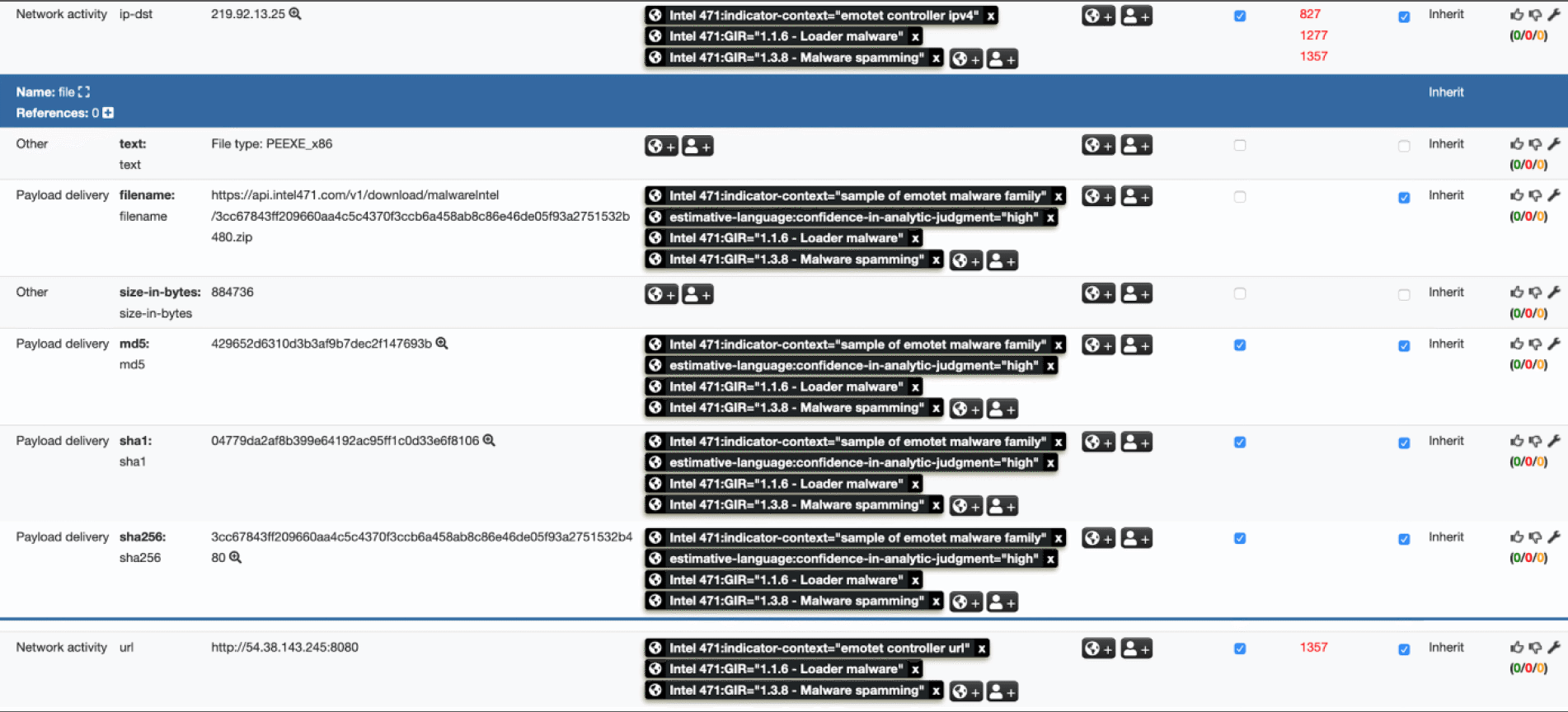
(Trickbot and Qbot) have shifted their focus to targeted ransomware attacks. A layered “defense-in-depth” approach is recommended to mitigate Emotet. One of the more effective defensive mechanisms is to proactively block all known Emotet controller IPs.
Without access to the control servers, Emotet is unable to perform its most dangerous functions. The bot’s primary goal, loading third-party malware, is nullified because payloads cannot be fetched from the controllers. The bot is also unable to download plug-ins that extend its functionality, such as those for lateral movement, credential stealing and email stealing. Without the ability to check in with the control servers, Emotet is no longer such a dangerous threat. An infection can more easily be cleaned up, since additional malware hasn’t been loaded.
Once pulled into your MISP instance, Emotet-related indicators can very easily be pushed to your IDS/SIEM.
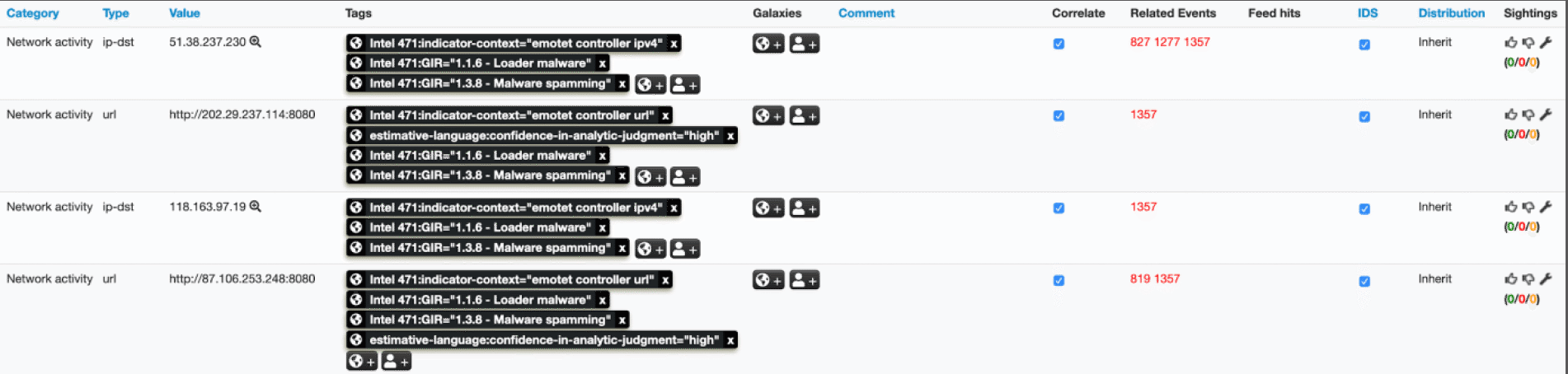
In addition to the standard MISP IDS attribute, the presence of the estimative-language:confidence-in-analytic-judgment=”high” tag against any given indicator signals it was validated as malicious by our Technical Research and Analysis Platform (TRAP) and should be a definite “block.” The absence of this tag means the indicator was observed but has yet to be validated during the owning MISP event’s referenced month. Thus, these indicators would be suitable candidates to “Alert.” If validation does occur, the tag will be applied and this will be synchronized to your MISP instance on the next pull from our feed.
Export from your MISP instance to any of the supported formats:
Subscribing to Our MISP Feeds
Making our feeds available in MISP format ensures you can take advantage of full MISP functionality and maximum data richness. Hooking up couldn’t be simpler – all you need is the feed URL, a username and a password. MISP takes care of everything else for you – no APIs to interact with or code to write!
Malware Freemium Offering
Intel 471’s MISP Malware Intelligence Freemium includes in-depth technical malware intelligence reports with ongoing tracking of the following malware families:
- AZORult
- Emotet
- Vidar
This includes a near real-time feed of the latest IoCs for these malware families.
Key Takeaways
Intel 471’s MISP integration delivers an easy mechanism to allow customers to consume our high-volume/high-fidelity intelligence. MISP then facilitates both in-platform analysis and correlation, coupled with the flexibility to transmit the data to where it’s needed. This powerful combination enables our customers to quickly identify the most relevant threats and helps them proactively defend their organizations.
Future Related Content
We’ll be continuing our series of MISP-related blogs and white papers in the near future. We’ll be taking a look at some of our other data sets that are available in MISP, such as “Vulnerability,” “Bulletproof Hosting” and “Adversary.”
Ten articles before and after
Global Trickbot disruption operation shows promise
Alleged REvil member spills details on group’s…
Ransomware-as-a-service: The pandemic within a pandemic
Here’s what happens after a business gets hit with…
That was quick: Trickbot is back after disruption…
Criminals posing as Lazarus Group threatened Travelex:…
Recent Trickbot disruption operation likely to have…