Key points
- Recent disruption actions against Trickbot likely will have only a short-term impact on Trickbot operations.
- Trickbot operators have multiple methods to avoid centralization of their command and control infrastructure which would make the botnet resilient to take down.
- If bogus data has been inserted into Trickbot as claimed and Trickbot operators are unable to filter out this bogus data, Trickbot-related intrusion activity may decrease in the short term.
- Trickbot is a sophisticated operation administered by skilled and experienced cybercriminals for many years. It is unlikely to be shut down without successful law enforcement action.
- Significant disruption of Trickbot likely would require an operation to remove infections en masse in conjunction with action against Trickbot’s servers, operators and infrastructure.
- Even in the unlikely event all current Trickbot-infected systems are disinfected en masse, the operators behind Trickbot will have little problem rebuilding the botnet with new infections.
Background
On Oct. 10, 2020, the Washington Post reported that “four U.S. officials” claimed U.S. Cyber Command was conducting an operation to disrupt the Trickbot botnet. This action first was identified by Intel 471’s Malware Intelligence systems Sept. 22, 2020. On Oct. 12, 2020, Microsoft announced legal action against Trickbot. An assessment of the outcomes of U.S. Cyber Command operation and Microsoft’s separate legal action against Trickbot up to Oct. 12, 2020, is contained within this report. We do not assess the future likelihood or future potential impact of U.S. Cyber Command or Microsoft carrying out additional action against Trickbot in this report.
Observed activity
The following is a chronology of activity that Intel 471 observed and previously reported:
SPOTREP published Sept. 22, 2020:
On Sept. 22, 2020, Malware Intelligence systems monitoring the Trickbot trojan malware detected a possible attempt to disrupt the Trickbot botnet. The Trickbot malware controllers issued bogus configurations to bots, listing the localhost address instead of real TrickBot controllers. Trickbot bots therefore were unable to “call home” to receive commands. Shortly after the bogus configs were pushed out, all Trickbot controllers stopped responding correctly to bot requests. This possibly means central Trickbot controller infrastructure was disrupted. The close timing of both events suggested an intentional disruption of Trickbot botnet operations. We will continue to monitor Trickbot behavior and report any additional state changes.
SPOTREP published Sept. 23, 2020:
On Sept. 22, 2020, the Trickbot operators showed signs of restoring their disabled botnet operations. The botnet was disrupted in the early morning of Sept. 22, 2020. The first signs of restoration were controllers responding to bot requests, although the controllers still were sending bogus configurations. Later on Sep. 22, 2020, Trickbot controllers began sending proper configs to any bots still checking in. The damage to the Trickbot botnet is unknown, but it is very likely several thousands of bots were lost. However, the controller infrastructure appeared to be stable now and Trickbot operations undoubtedly will resume. We assess this act of sabotage most likely to be the work of a vigilante researcher, although other scenarios also are possible.
SPOTREP published Oct. 1, 2020:
Early on Oct. 1, 2020, Intel 471 Malware Intelligence systems monitoring the Trickbot trojan detected a second possible attempt to disrupt the Trickbot botnet. Much the same way as the first attempt Sept. 22, 2020, Trickbot malware controllers issued false configurations to bots listing the local host address instead of real Trickbot controllers. Several hours elapsed before the botnet operation was restored after the first disruption attempt, which possibly resulted in the loss of many bots from the botnet. We continue to monitor Trickbot behavior and intend to report any additional state changes.
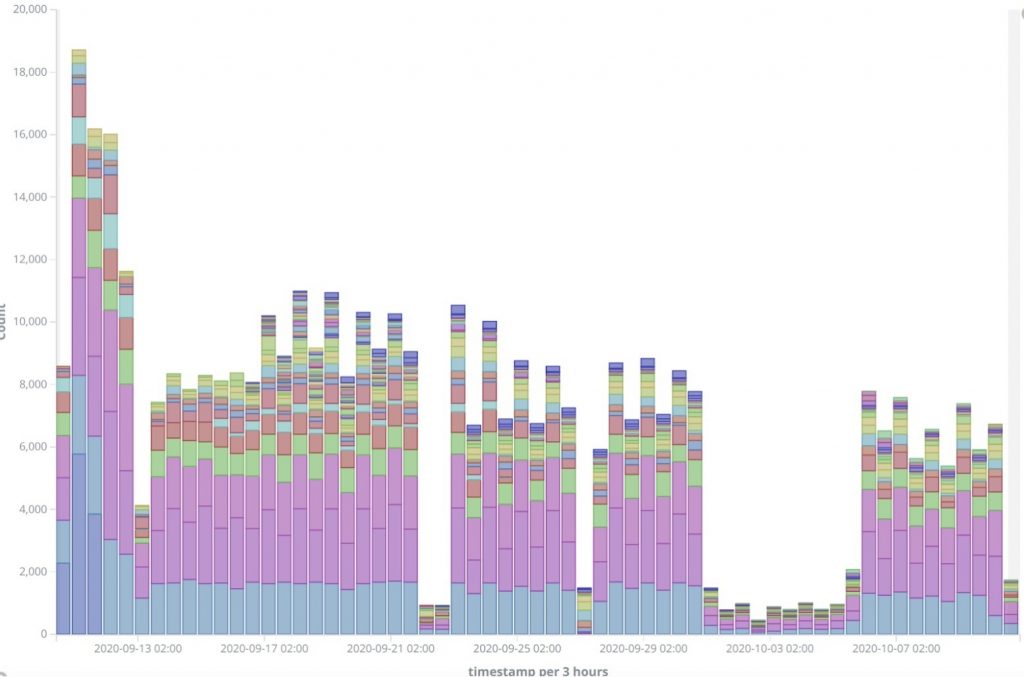
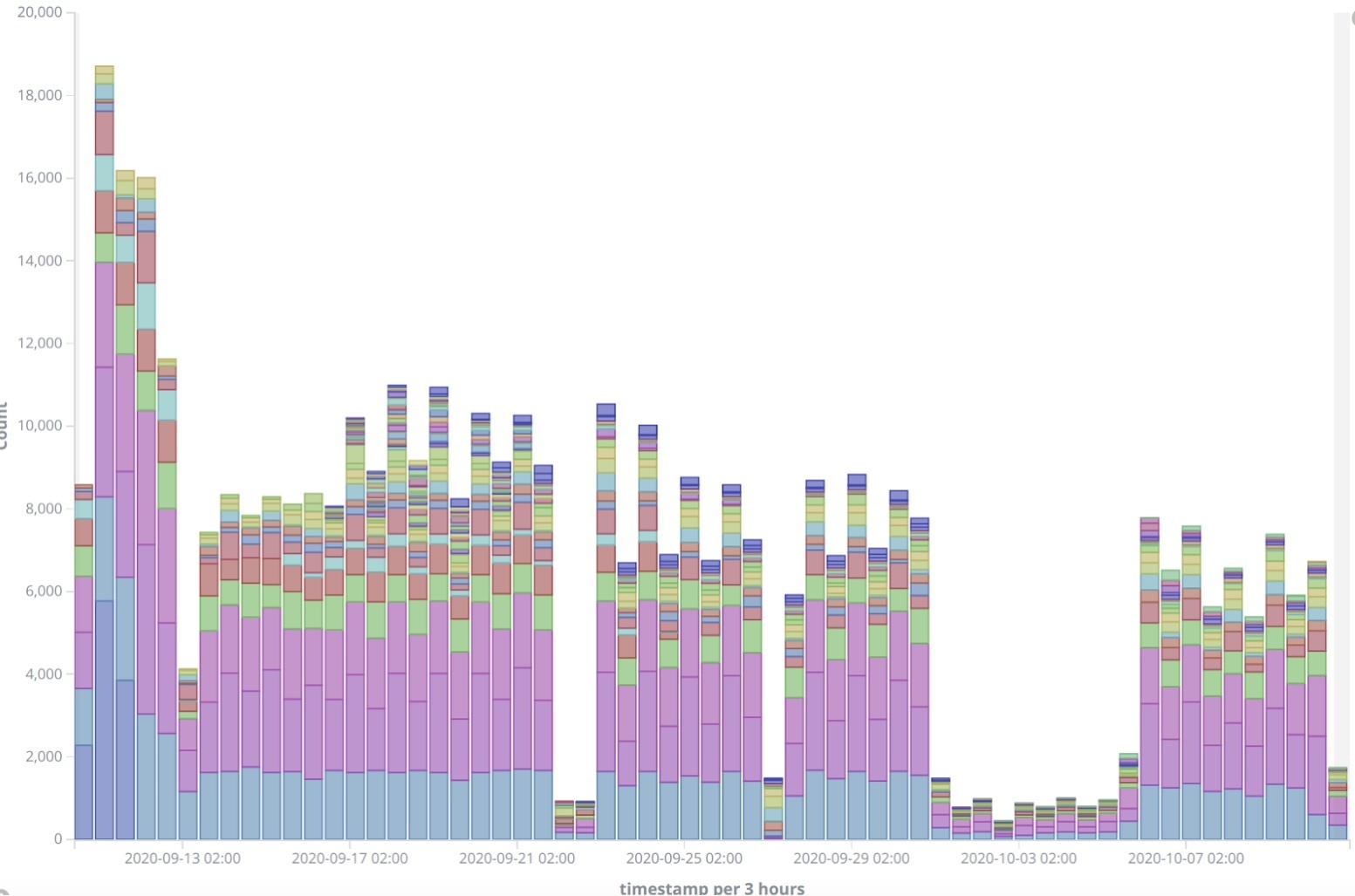
Figure 1 below shows unique Trickbot controllers responding to emulated bots via our Malware Emulation and Tracking System (METS) between Sept. 10, 2020 and Oct. 10, 2020. Disruption activity, illustrated by the significant drop in controller responses, can clearly be seen starting on both Sept. 22, 2020 and Oct. 1, 2020.
Trickbot command and control servers disrupted by Microsoft
On Oct. 12, 2020, Microsoft issued a public statement that they had taken legal action to “combat ransomware ahead of U.S. elections.” The legal action involved Microsoft attempting to disrupt a number of Trickbot command and control server IP addresses that are in the United States. See Appendix 1 – Command and control servers Microsoft is attempting to disrupt for information on the specific IP addresses that Microsoft was attempting to disrupt. Since Aug. 1, 2020, Intel 471 has seen 579 unique IP addresses that were listed by the Trickbot operators as Trickbot command and control servers. Of those 579 IP addresses, Intel 471 was able to validate that 60 IP addresses were active and working Trickbot command and control servers.
Trickbot status as of Oct. 12, 2020
A review of current Trickbot activity revealed that at the time of this report, 50 unique IP addresses currently are being listed by the Trickbot operators as Trickbot command and control servers. On Oct. 12, 2020, and of the 50 IP addresses, Intel 471 confirmed a total of 19 unique Trickbot control servers were active and working. Microsoft’s list of Trickbot IP addresses contained four IP addresses at the time of this report and were being pushed by Trickbot’s operators as Trickbot command and control servers. At the time of this report, Intel 471 has not seen any significant impact on Trickbot’s infrastructure and ability to communicate with Trickbot-infected systems.
Trickbot uses decentralized infrastructure to avoid takedowns
Trickbot’s primary command and control mechanism supports communication over the Onion Router (Tor) and a fall-back method that uses the decentralized domain name system EmerDNS. As a result, it is highly likely a takedown of the Trickbot infrastructure would have little medium- to long-term impact on the operation of Trickbot.
EmerDNS provides the Trickbot operators with a setup that is decentralized, has no single-controlling entity and is resilient to takedown. In the event all Trickbot infrastructure is taken down, the cybercriminals behind Trickbot will need to rebuild their servers and change their EmerDNS domain to point to their new servers. Compromised systems then should be able to connect to the new Trickbot infrastructure.
Trickbot’s EmerDNS fallback domain safetrust.bazar recently resolved to the IP address 195.123.237.156. Not coincidentally, this network neighborhood also hosts Bazar malware control servers. Researchers previously attributed the development of the Bazar malware family to the same group behind Trickbot, due to code similarities with the Anchor malware family and its methods of operation, such as shared infrastructure between Anchor and Bazar. On Oct. 12, 2020, the fallback domain resolved to the IP address 23.92.93.233, which was confirmed by Intel 471 Malware Intelligence systems to be a Trickbot controller URL in May 2019. This suggests the fallback domain still was controlled by the Trickbot operators at the time of this report.
Bogus data reportedly inserted into Trickbot’s servers could reduce Trickbot derived intrusion activity in the short term
On Oct. 2, 2020, Brian Krebs reported on the disruption attempts against Trickbot. While we are unable to verify the information, Alex Holden of Hold Security claimed someone “is flooding the Trickbot system with fake data” and that the records generated include “machine names indicating these are infected systems in a broad range of organizations.” Intel 471 believes the operators and customers of Trickbot are experienced in triaging the large amount of compromised systems to find systems of interest for subsequent and manually driven intrusion activity depending on the target. For example, on Sept. 16, 2020, Intel 471 publicly reported access to infected systems associated with financial institutions occasionally was being provided to North Korean threat actors.
Since we are unable to verify the information, we are unable to assess whether inserted bogus data can be easily filtered out by the Trickbot operators or whether the insertion of bogus data into Trickbot’s servers is continuing. We also are unable to assess how bogus data may have been inserted, i.e., via direct access to the database or via emulating real victims connecting to Trickbot command-and-control servers. If bogus data has been inserted and it is indistinguishable from real data, Trickbot-related intrusion activity should be reduced in the immediate future.
Significant disruption requires removing Trickbot infections en masse in conjunction with action against Trickbot servers, operators and infrastructure
Given that Trickbot’s operators implemented decentralized command-and-control methods, one of the only viable options to impact current Trickbot infections en masse is to push an update to all infected systems that would remove Trickbot itself. Legal and ethical issues withstanding, this would disrupt the operations of Trickbot until they were able to obtain new infections. Simultaneous offensive action against Trickbot servers, operators and infrastructure also could disrupt their operations further. A denial-of-service attack is one example of an offensive disruption approach that could be undertaken but this also has ethical and legal considerations to consider.
Trickbot operators continue to be able to obtain new infections
Trickbot is spread by several different groups that often employ distinct methods with its primary spreading method being via spam emails. Without major action against Trickbot’s core infrastructure the groups leveraging the malware will be able to replenish their numbers in a relatively short period of time.
Trickbot likely will not be stopped without successful and coordinated law enforcement action
Trickbot is a large, well-established and long-running criminal operation which will remain difficult to stop without coordination, cooperation and action with numerous stakeholders including international law enforcement, governments and the security community.
Changing the calculus of cybercriminals requires novel solutions
Western law enforcement has embraced public indictments to remove the anonymity of cybercriminals who consider themselves safe from apprehension. Regardless of that, deterring cybercriminals in overseas jurisdictions that do not cooperate with western law enforcement requires novel solutions. Examples of this could include direct targeting of cybercriminals’ personal computers, releasing their personal information publicly and targeting of their financial assets. It is expected cybercriminals would hold considerable sums of funds within cryptocurrencies which could be impacted through offensive operations and asset seizures.
Appendix 1 – Command and control servers Microsoft is attempting to disrupt
Microsoft submitted a court order to disrupt the below IP addresses:
| IP Address | Last Activity | Intel 471 Description |
| 104.161.32.103 | 2020-10-06 | Bazar and Trickbot controllers |
| 104.161.32.105 | 2020-10-12 | Trickbot controller |
| 104.161.32.106 | 2020-10-12 | Trickbot controller |
| 104.161.32.109 | 2020-07-13 | Trickbot controller |
| 104.161.32.118 | 2020-10-12 | Trickbot controller |
| 104.193.252.221 | 2020-09-24 | Emotet download location (used by Trickbot to download Emotet) |
| 107.155.137.19 | 2020-04-19 | Trickbot controller |
| 107.155.137.28 | 2020-09-25 | Trickbot controller |
| 107.155.137.7 | 2020-10-06 | Bazar and Trickbot controllers |
| 162.216.0.163 | 2020-05-28 | Trickbot download location (used to distribute Trickbot) |
| 23.239.84.132 | 2020-10-06 | Bazar and Trickbot controllers |
| 107.174.192.162 | 2020-10-12 | Trickbot controller |
| 107.175.184.201 | 2020-09-29 | Trickbot controller |
| 139.60.163.45 | 2020-09-30 | Bazar and Trickbot controllers |
| 156.96.46.27 | N/A | Unknown |
| 195.123.241.13 | 2020-10-12 | Trickbot controller |
| 195.123.241.55 | 2020-10-12 | Trickbot controller |
| 162.247.155.165 | 2020-06-24 | Trickbot controller |
Ten articles before and after
Criminals posing as Lazarus Group threatened Travelex:…
That was quick: Trickbot is back after disruption…
Leveraging Intel 471’s Malware Intelligence Data using…
Global Trickbot disruption operation shows promise
Alleged REvil member spills details on group’s…
Partners in crime: North Koreans and elite…
Prioritizing “critical” vulnerabilities: A threat…
Flowspec – TA505’s bulletproof hoster of choice