Coronavirus Disease 2019 (COVID-19) continues to surround our everyday lives and its presence remains a topic of interest and discussion within underground forums. In the earlier days of the pandemic, we took a look at how attackers were leveraging the fear surrounding the disease to launch campaigns such as business email compromise (BEC), phishing and malicious domains, but questions remain about how or whether the marketplace has been directly impacted. Some may think the underground economy for malware and stolen access and data took a hit similar to Wall Street, however, that is not the case. A few threat actors allegedly used the pandemic to join or spend more time on underground forums which could have increased the demand for or availability of data and services slightly, but there is no significant activity to support this assessment at this time. Additionally, there were a few low-tier actors who claimed to adjust pricing due to COVID-19, but overall there were no significant changes in malware or data prices due to the pandemic.
Impact to underground economy
Demand and availability of accesses, compromised data, and malware
Very much like a number of you reading this blog are spending more time in front of your computer screen, a number of threat actors claimed to have joined or spent an increased amount of time on underground marketplaces due to the virus and subsequent result of more “free time.” For instance, one threat actor claimed COVID-19 allowed him or her to offer free hacking services, and a few other actors stated they lost their jobs or lacked funds due to the pandemic and sought or offered work on underground forums. Threat actors also have considered how certain cybercrime might be easier to commit or more widespread due to the virus. In late March 2020, a discussion related to COVID-19 amongst two carders suggested that carding could be more successful and easier due to business transitioning to online shopping only. While such activity could increase the demand and availability slightly, there wasn’t any related significant activity at the time of this blog.
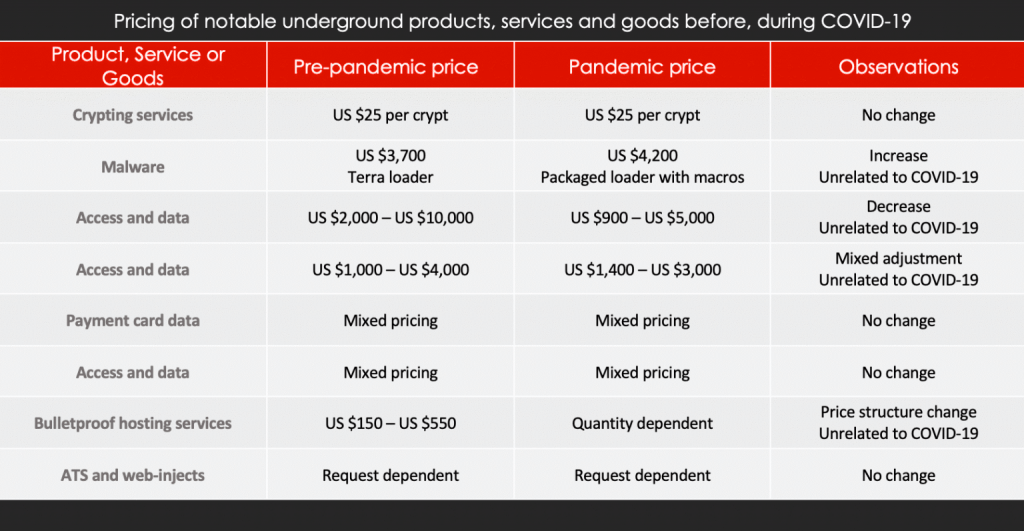
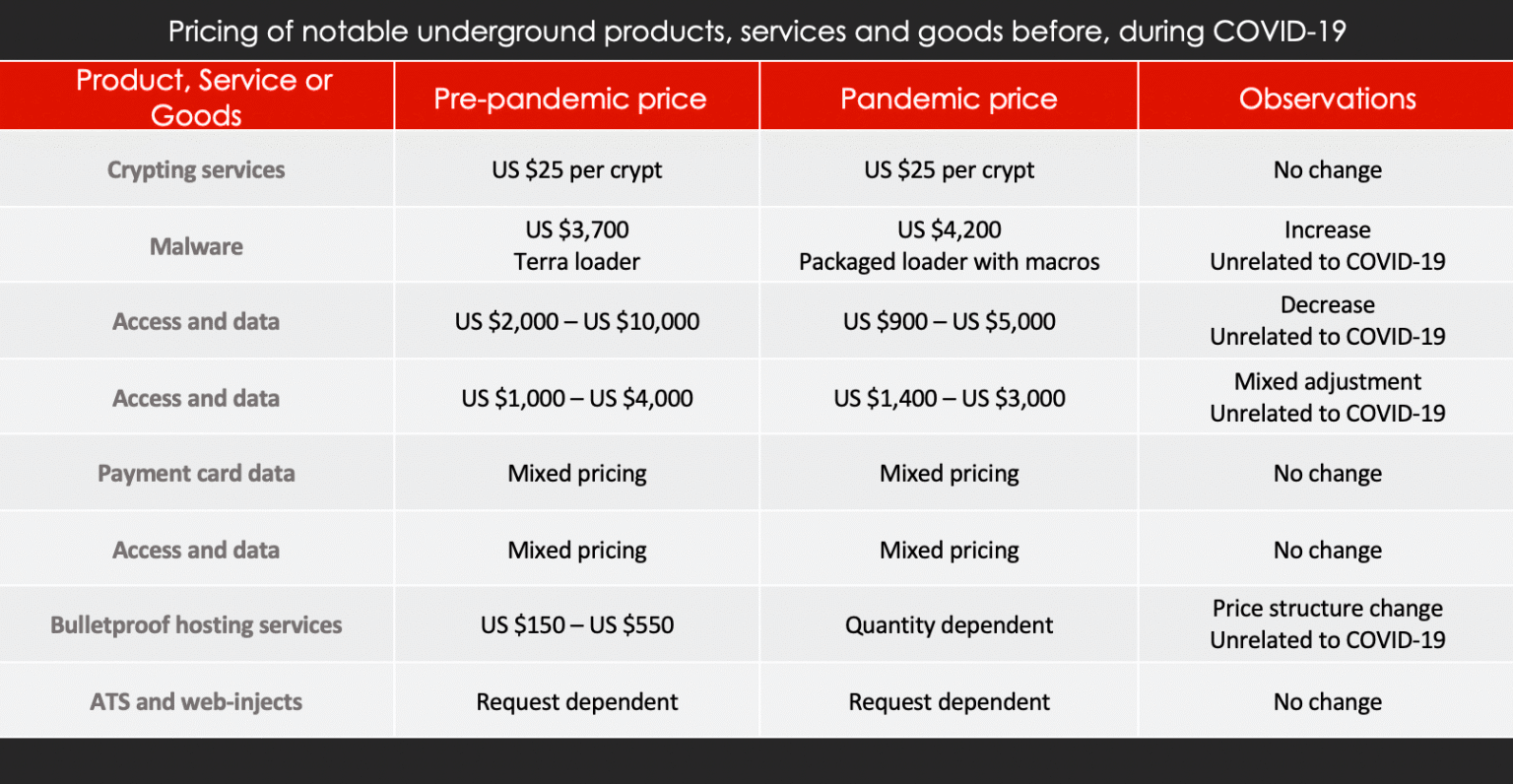
Pricing of access, data, malware
Research on a handful of top-tier actors focused on malware, stolen credit card shops, call service and hacked accesses showed no significant change in prices of the actors’ offers pre-pandemic versus during COVID-19. The actor behind the Terra malware loader continues to sell and support the product which was priced at US $3,700 prior to the pandemic. During the COVID-19 outbreak, the actor attempted to sell the malware loader in a package with malicious macros and priced the tool at US $4,200. This increase in price likely was due to the “package” offer that included new features rather than an impact of the virus and the actor seeking increased funds. Additionally, another notorious actor that specializes in selling hacked accesses reemerged in the underground during the pandemic and advertised several new accesses for sale. The price sat within the range the actor previously sought for similar offers advertised before COVID-19. While the recent reappearance of the actor could be viewed as the actor seeking more money during a difficult time, it’s likely he had merely taken time away from forum activity to work on gaining new access, therefore, the timing of the new sales threads simply might be coincidental.
Although they are in the minority, a few threat actors adjusted prices for their offers due to the pandemic. In April, a well-known call service adjusted prices as a result of the virus’ impact on service times. The actor claimed there was an average 20 to 25-minute wait on calls for FedEx and UPS, therefore, the new price for calls would be adjusted to US $7 “regardless of the outcome.” It appears the minimal observations in price changes due to the pandemic primarily are attributed to low-level threat actors, but pricing on malware and stolen access and data offered by more prolific adversaries persists unchanged.
Key Observations
While the impact of the pandemic on everyday life has been quite significant, its influence in the underground marketplace appears to be less than initially expected by some. A large part of what makes the legal economy run is face-to-face interaction, which has been disrupted, but the underground economy is built on minimal in-person exchanges. Since the start of COVID-19 in late 2019, the underground appeared to operate under business as usual, with some threat actors claiming to join or spend more time on forums and a few others adjusting the price of goods and services due to the virus. Overall, observations suggest there were no significant changes in malware and data prices or increase in demand for and availability of data and services due to the pandemic.
Ten articles before and after
Iran’s domestic espionage: Lessons from recent data…
Flowspec – TA505’s bulletproof hoster of choice
Prioritizing “critical” vulnerabilities: A threat…
Partners in crime: North Koreans and elite…
Recent Trickbot disruption operation likely to have…
You need to adjust your patch priorities!
Changes in REvil ransomware version 2.2