
Some business people might say the security folks don’t understand the dollar impact of taking a system offline. The reality is in business often time is money and quantifying the cost of key systems being taken offline is a real thing. Some security folks might also say that your business folks don’t understand or care about the risk or impact of a vulnerability being exploited. This is an age-old situation that pits two competing worlds where one side might be more comfortable with taking risks and the other tends to be more risk averse. Queue your cyber threat intelligence team…the perfect referee in this conversation.
Patching decisions must be based on a solid (as possible) calculation of risk to your organization associated with a subject vulnerability. Everyone’s probably sick of hearing about the risk equation, but let’s revisit it just one more time for the sake of this conversation:
RISK = IMPACT * PROBABILITY / COST
Measuring impact and cost are often an internal facing exercise encompassing data that is readily available as long as the right people are at the table. We’re going to focus on measuring the more abstract concept of probability given a particular vulnerability. Some will focus on the vulnerabiliy’s CVSS score, but this is merely a standalone measure of severity of the vulnerability. There’s little to no context or business realities being taken into account with the CVSS. It’s simply not a measure of risk and even the CVSS 3.1 standard itself tells us we shouldn’t rely on it as a measure of risk:
“The CVSS Specification Document has been updated to emphasize and clarify the fact that CVSS is designed to measure the severity of a vulnerability and should not be used alone to assess risk.”
Source: https://www.first.org/cvss/use…
Supporting an assessment of probability is the perfect situation to leverage Threat Intelligence. This is where some of your known unknowns become known. If you are asking your CTI team or vendors to support vulnerability management and patch prioritization you should be asking the below questions. If your CTI capability is not supporting vulnerability management and patch prioritization you need to ask why not!
Intelligence requirements to support patch prioritization:
- What is the level of interest in open sources, the underground and privately amongst cybercriminals?
- Is proof-of-concept (POC) code being traded or for sale in the underground, in open sources or privately between cybercriminals?
- Have attacks in the wild been observed?
- Has the exploit been weaponized?
- Has an exploit been productized into a known exploitation framework or kit?
- Lastly, some like to take volumetric keyword hits against vulnerability terms or CVEs, but the problem is this often lacks context. If you are truly going to have intelligence support to patch prioritization you need context – actual conversations amongst threat actors, assessments and history to assess threat actor capabilities and intent, etc.
For example, here’s what we call a SPOTREP* that we sent out to our clients that would have been routed to anyone subscribed to our Vulnerability and Exploits General Intelligence Requirements (GIRs):
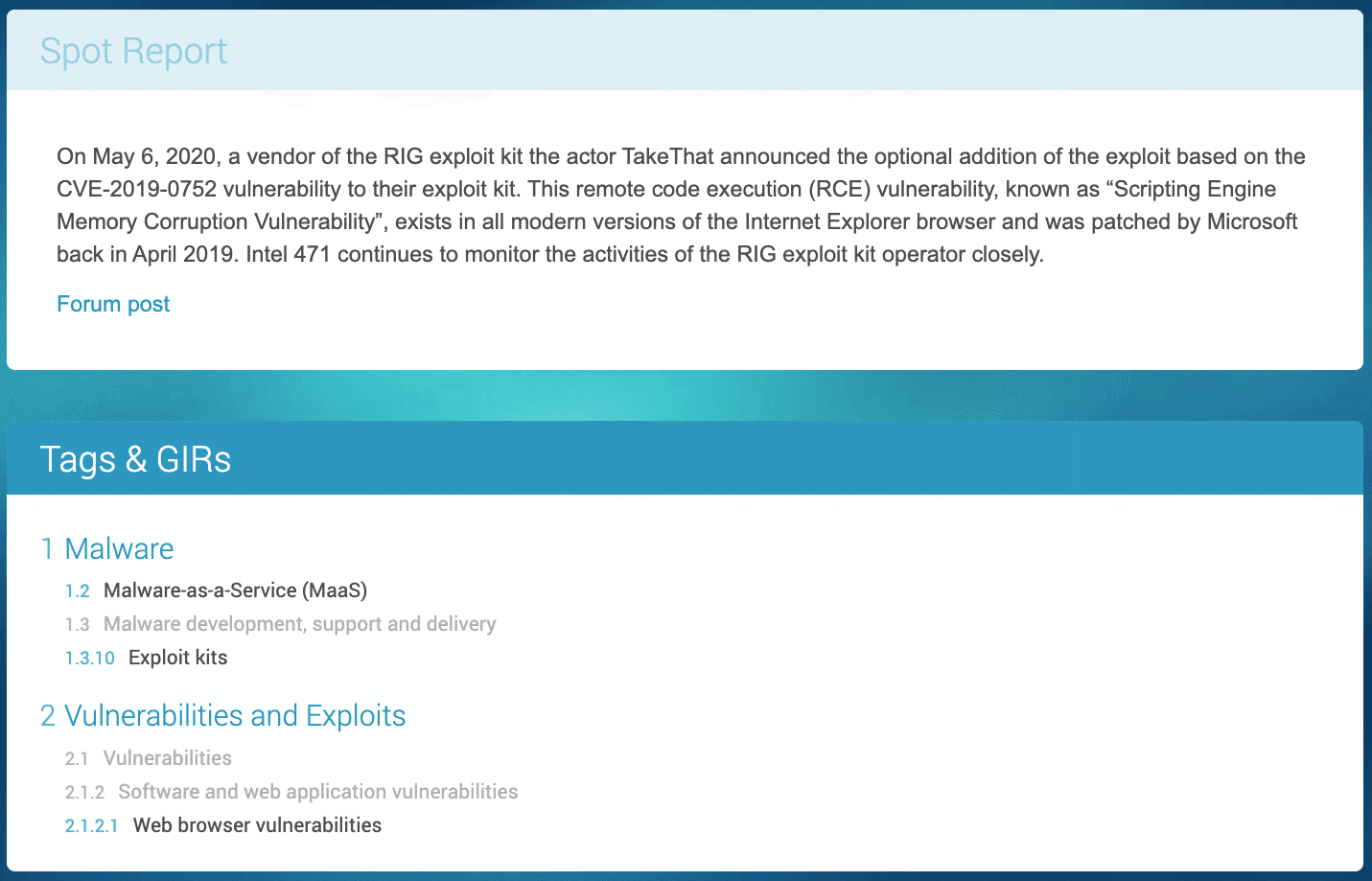
We have a significant threat actor who has communicated to the market that a specific vulnerability was integrated into a widely used exploit kit. The barrier to entry to leverage this exploit dropped significantly. If this sort of data point and context doesn’t help drive the probability equation and assessment of risk in general then there may not be much else that will. This sort of information can be leveraged regularly and should be. Lean on your CTI teams and vendors to support the very important use-case of patch prioritization. CTI teams reach out to your vulnerability managers and show them how you can support their use-case and the business overall.
Want to see an example of Vulnerability Intelligence? Please consider subscribing to our Periscope list and get a monthly version of Intel 471’s CVE Weaponization Report, which is curated by Intel 471 analysts who track the life cycle of vulnerabilities from initial disclosure to exploit weaponization and productization observed in the underground. You can read more about it here: www.intel471.com/periscope.html.
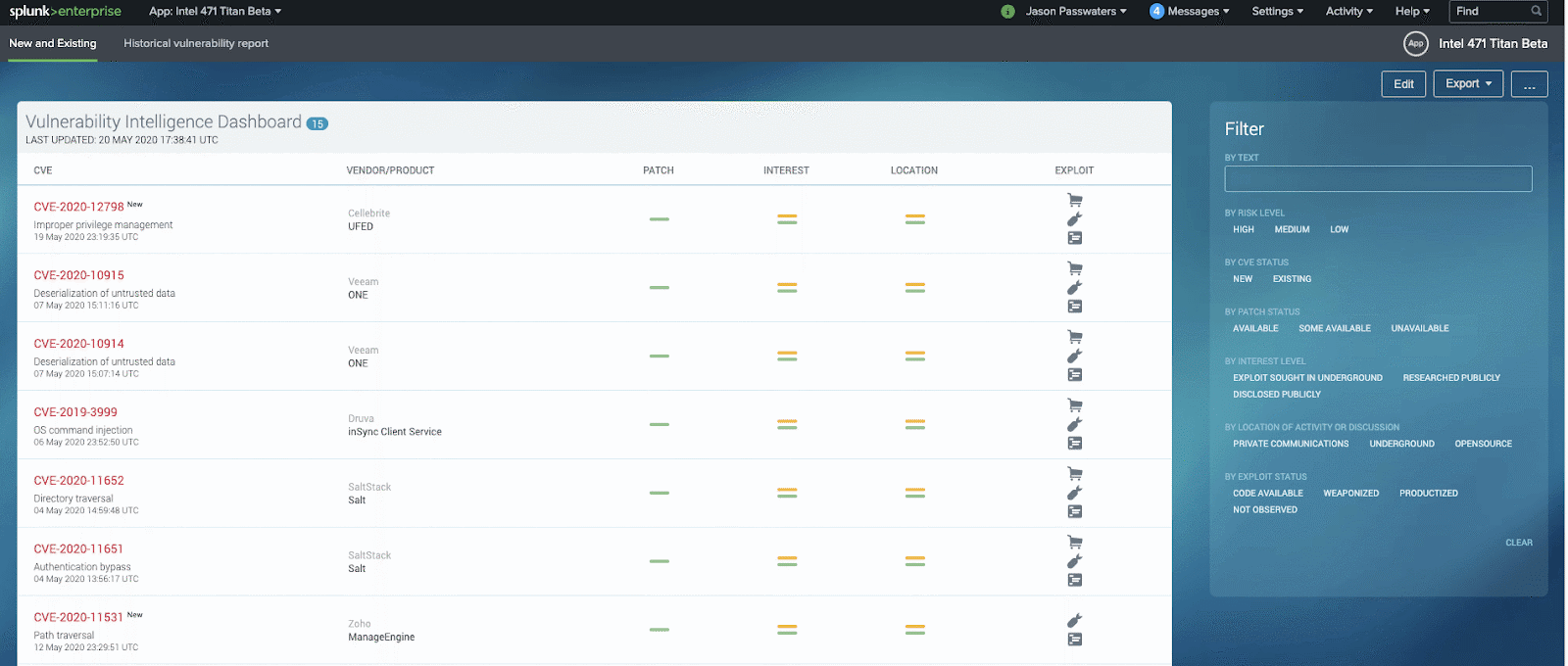
Lastly, we’re finalizing our Vulnerability Intelligence Splunk Application so please stay tuned on splunkbase.com for more information. It will be a Splunk version of our live Vulnerability Intelligence dashboard found in our Titan platform. Here’s a teaser….
Ten articles before and after
Coronavirus having minimal impact on prices, demand,…
Iran’s domestic espionage: Lessons from recent data…
Flowspec – TA505’s bulletproof hoster of choice
Prioritizing “critical” vulnerabilities: A threat…
Partners in crime: North Koreans and elite…
Changes in REvil ransomware version 2.2
COVID-19 pandemic: Through the eyes of a cybercriminal
