There’s been a shift in the ransomware-as-a-service ecosystem.
Be it due to law enforcement, infighting amongst groups or people abandoning variants altogether, the RaaS groups dominating the ecosystem at this point in time are completely different than just a few months ago. Yet, even with the shift in the variants, ransomware incidents as a whole are still on the rise.
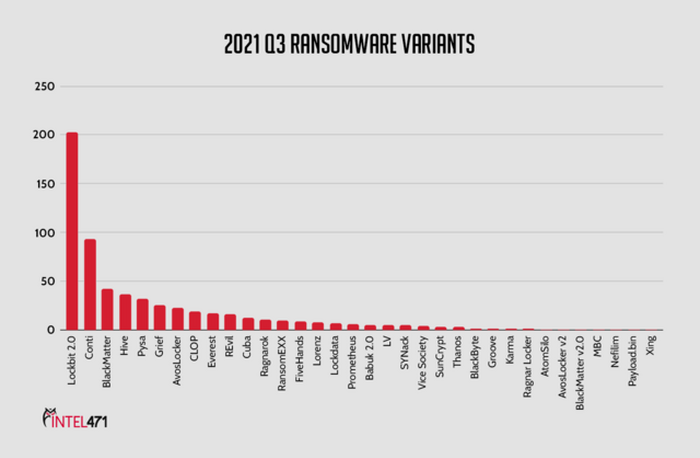
From July to September 2021, Intel 471 observed 612 ransomware attacks that can be attributed to 35 different ransomware variants. Among those attacks, several lesser-known variants have supplanted prominent ones that rose in notoriety over the first half of 2021.
Of the attacks Intel 471 observed approximately 60 percent were tied to four variants. One in particular — Lockbit 2.0 — was responsible for approximately one-third of observed attacks.
The most prevalent variants from July-September 2021 were:
|
Ransomware Group |
Percent of Attacks JUL-SEP ‘21 |
|
LockBit 2.0 |
33% |
|
Conti |
15.2% |
|
BlackMatter |
6.9% |
|
Hive |
6% |
The most-impacted sectors were manufacturing, consumer and industrial products, professional services and consulting and real estate. While the life sciences and health care, financial services and nonprofit sectors were impacted to a lesser extent.
LOCKBIT 2.0
The LockBit 2.0 ransomware variant was the most prominent in the third quarter of 2021, despite only being discovered in the wild in June 2021. The variant rose six months after the original LockBit went dark in late 2020, which In terms of total events observed, manufacturing was the most impacted sector at 24 percent, followed by the consumer and industrial products sector at 20.2 percent, and the professional services and consulting sector at 18 percent.
The most notable attack tied to Lockbit 2.0 during this time period was the ransomware attack on global consulting firm Accenture, which showcased a number of tactics the group uses to inflict damage on organizations. After launching the ransomware, Intel 471 learned that the actors responsible for the attack also hit the company with a DDoS attack to further press the victim into negotiations and bring additional media attention to the matter. Additionally, attackers dumped data stolen in the attack onto a name-and-shame blog in the hopes of inflicting pressure to pay a ransom. Those behind the attack initially asked for $50 million in ransom before launching their subsequent attacks in a tactic known as “double extortion.”
CONTI
While Conti has consistently been one of the most active RaaS variants in use this year, the amount of attacks in which it was used dipped approximately 64 percent when compared to the second quarter of 2021. This could be partly due to the operators not regularly updating and releasing victims’ data on their public blog. In August, an actor leaked training documents and exposed some infrastructure that revealed two other actors’ roles in running the variant, allegedly due to the operators not paying network access brokers their cut of ransom payments. The initial actor and one of the doxxed actors were booted from the forum after being tied to ransomware operations.
However, the variant was observed in nearly 100 incidents Intel 471 tracked. Conti was used to target the manufacturing sector for 22 percent of attacks, followed by the consumer and industrial products sector at 21 percent, the professional services and consulting sector at 20 percent and the technology, media and telecommunications sector at 11 percent. The countries most impacted by Conti this quarter were the U.S. at 53 percent, France at 8 percent, Canada at 6 percent and Germany at 5 percent.
We will be watching Conti closely over the next few months as there may be some upheaval for the group. In November, a security company exploited a vulnerability in Conti’s infrastructure that allowed them to gain a wealth of information on the group’s operations, including hidden IP address, victim chat logs, and bitcoin wallets used to collect ransoms. The report also tied Conti to Ryuk, a ransomware variant that was used in thousands of attacks over the past few years.
BLACKMATTER
While BlackMatter ransomware first was observed in July 2021, there are signs that this variant has been around for some time, albeit under a different name. Many cybersecurity vendors have concluded that BlackMatter most likely originated from the DarkSide ransomware variant, based on several technical code similarities, the style of the victim name-and-shame blogs and several other linguistic indicators. Additionally, a cybersecurity researcher identified that BlackMatter uses the same unique encryption method DarkSide previously used. Another link between the two variants was uncovered by blockchain firm Chainalysis blockchain when researchers discovered cryptocurrency wallets that overlapped between the two groups.
DarkSide was the ransomware variant used in the Colonial Pipeline attack, which led to a partial shutdown of U.S. gasoline delivery and a week of panic-induced shortages in several states. After the attack, the group said it would stop targeting critical infrastructure, along with several forums banning ransomware advertisements on the sites.
Despite the upheaval, the variant was used in more than 40 attacks in the measured time period, with the most notable attack hitting Japanese audio-visual hardware company Olympus. Of the attacks observed, the hardest-hit sectors were consumer and industrial products, and life sciences and health care.
HIVE
Hive is a relatively new RaaS affiliate, having been discovered in June 2021. The affiliates rely on a name-and-shame blog to add pressure to victims, including posts about the date of initial compromise, a countdown timer and the date the leak was disclosed on the site. Additionally, Hive operators sometimes include the option to share the disclosed leak on social media.
The variant has been tied to several attacks on hospital systems in the U.S., including several hospitals on the West Virginia-Ohio border. Additionally, attackers in September went after a hospital system in Missouri.
Despite the health care focus, the most-impacted sector was consumer and industrial products (18 percent of Hive’s attacks) The next three sectors — manufacturing, professional services and consulting, real estate and technology, and media and telecommunications — were tied at 13 percent each. The Life sciences and health care sector accounted for 8 percent.
The U.S. was the most-impacted country, accounting for about 62 percent of all Hive events reported, followed by the U.K. at 5 percent. Intel 471 observed attacks in 12 other countries — Australia, China, Germany, India, the Netherlands, Norway, Peru, Portugal, Spain, Switzerland, Taiwan and Thailand — that amounted to nearly 3 percent per country.
Receding ransomware variants
The rise in the ransomware variants Intel 471 has tracked comes as some more notable variants of years past have faded into obscurity. While it’s common practice for ransomware groups to suddenly disappear and re-emerge under a new name, groups’ motives for doing so aren’t well-known. The past few months have been different: we’ve seen several groups go quiet after external actions have forced groups to slow down operations or shut down altogether.
CLOP
This RaaS affiliate, which has long been linked with TA505, was relatively quiet in the time period measured by Intel 471. Over the three months we observed attacks, CLOP was used in approximately 20, with some ending in million-dollar ransoms being paid out. Even while launching attacks, the group has been changing infrastructure relatively quickly. From September, the group switched the .onion domains it uses for its victim leak blog and file hosting services it uses to launch attacks. Additionally, Intel 471 also observed the group engaging in “double extortion” attacks, mostly by sening “warning emails” to the victim’s business partners and clients.
However, time may be running out for the variant’s developers. Earlier this year, a multi-group law enforcement effort led to the arrest of six suspects in 20 raids across Ukraine, seizing computers, technology, cars, and roughly $185,000. While the arrested suspects were not thought to be directly responsible for CLOP’s operation, the crew has slowed in the amount of attacks that have been launched since the arrests.
REVIL
The notorious ransomware group went quiet in July after it was discovered that the group was responsible for two high-profile attacks: one on multinational meat supplier JBS and the other on third-party IT provider Kaseya. After a short return in September, a pair of operations that hijacked REvil’s infrastructure — carried out by U.S. Cyber Command and another unknown foreign government — caused the variant’s operators to abandon their affiliates and any further attacks out of fear of being caught by law enforcement.
Additionally, the U.S. announced two members of the crew — Yaroslav Vasinskyi, a 22-year-old Ukrainian national, and Yevgeniy Polyanin, a 28-year-old Russian national — were indicted for their roles in REvil attacks ranging all the way back to 2019.
Intel 471 has not seen any ransomware-related activity from REVil since October 14, days before REvil developers announced the end of their affiliate program.
RESULTS
The charts below are what Intel 471 saw over the three-month measuring period. To better understand these numbers, it’s important to take into account the way the ransomware ecosystem operates. Many of these variants are run by developers who give access to affiliates, who may behave differently from attack to attack. Furthermore, since threat actors can become affiliates of multiple ransomware services at the same time, it can be difficult to correlate specific TTPs to one specific ransomware service or make definitive claims on how each group behaves. These numbers are focused on the amount of events we witnessed, what variant was responsible, and what sector victim organizations belong to.


CONCLUSION
Ransomware continues to be a prevalent threat with no signs of waning. While law enforcement around the world has gotten more aggressive in their efforts to arrest those behind attacks, developers are still easily shutting down popular variants, laying low, and coming back with finely-tuned malware used by themselves as well as affiliates. As long as the developers can remain in countries where they are granted safe harbor, the attacks will continue, albeit with different variants. No matter what malware is ultimately deployed, the same defensive tactics that were used to thwart previous variants apply to those we catalogued above.
Cybersecurity teams inside organizations must understand that being proactive in their defensive posture while also understanding how the cybercriminal underground is shifting its own tactics, is crucial to protect themselves from a devastating ransomware attack.
Ten articles before and after
Here’s how the cybercriminal underground has reacted…
Introducing uCrop, Our Own Image Cropping Library for Android
How We Created uCrop, Our Own Image Cropping Library for Android
Introducing Horizon, Our Open Source Library for Sound Visualization
Using Machine Learning Algorithm for Predicting House Valuations
How the new Emotet differs from previous versions
Emotet is back. Here's what we know.
How cryptomixers allow cybercriminals to clean their…