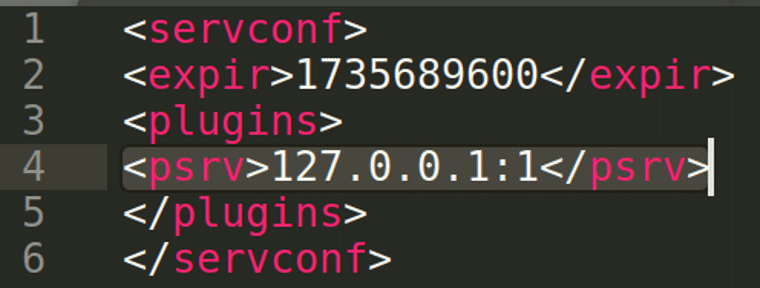
Changes in REvil ransomware version 2.2
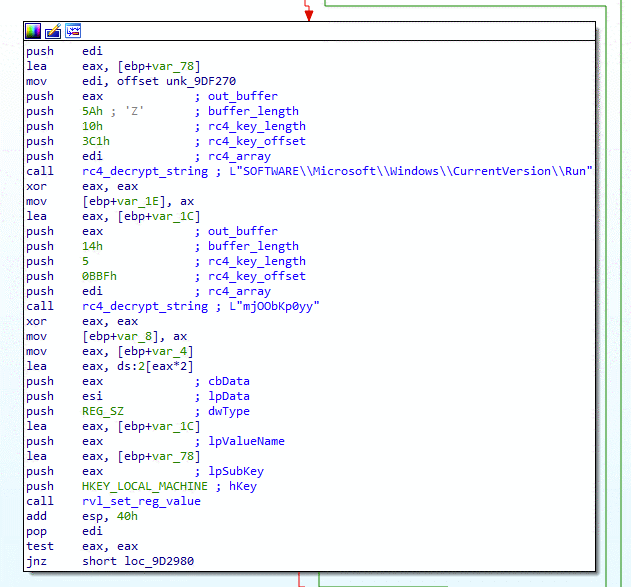
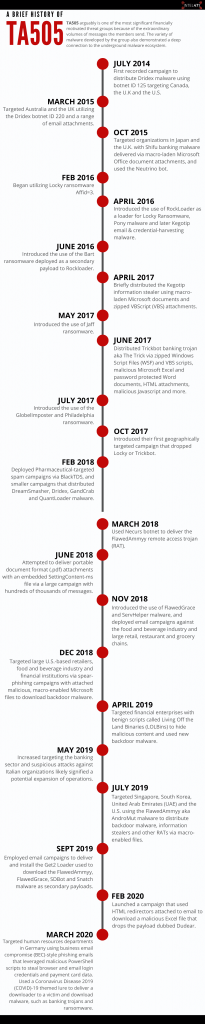
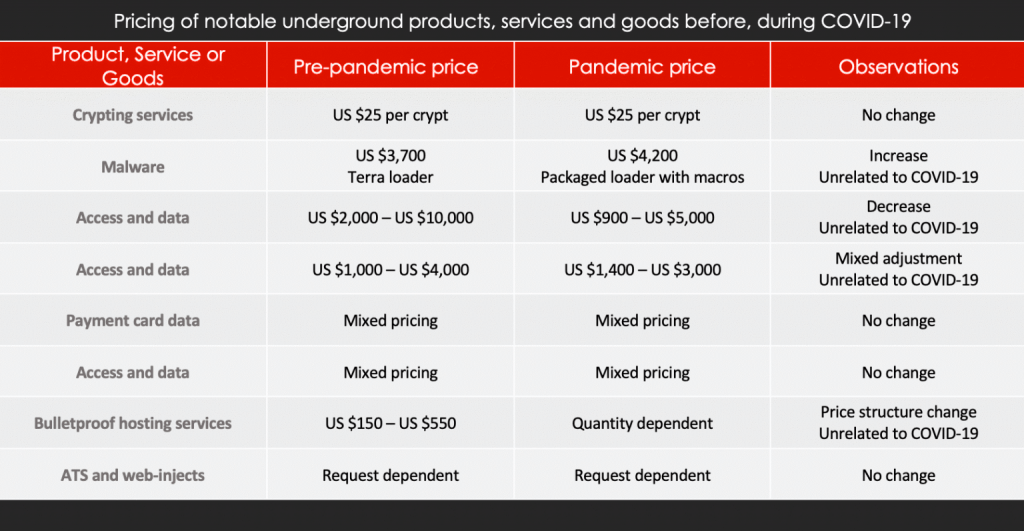
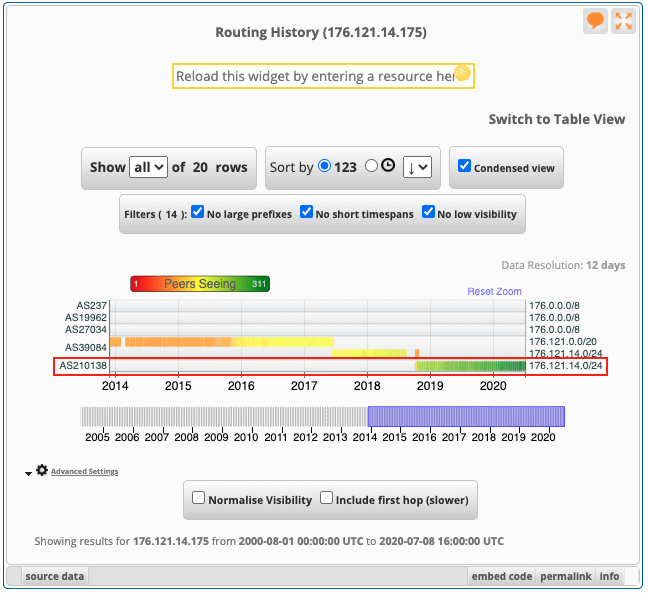
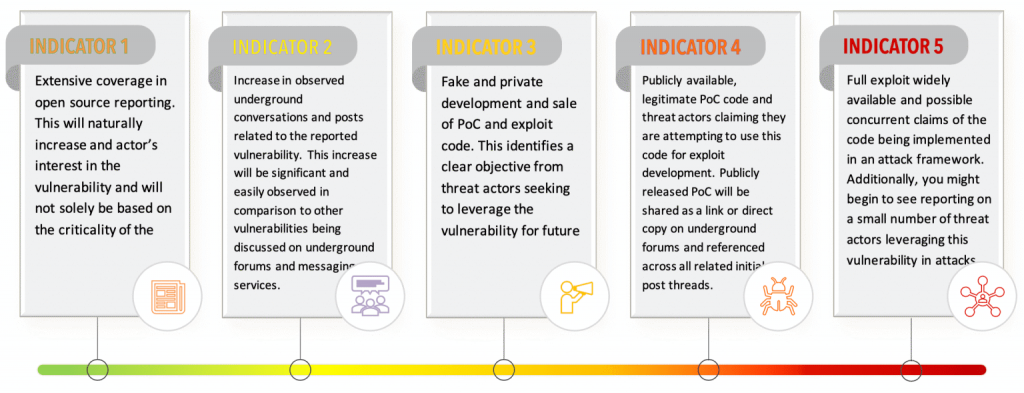
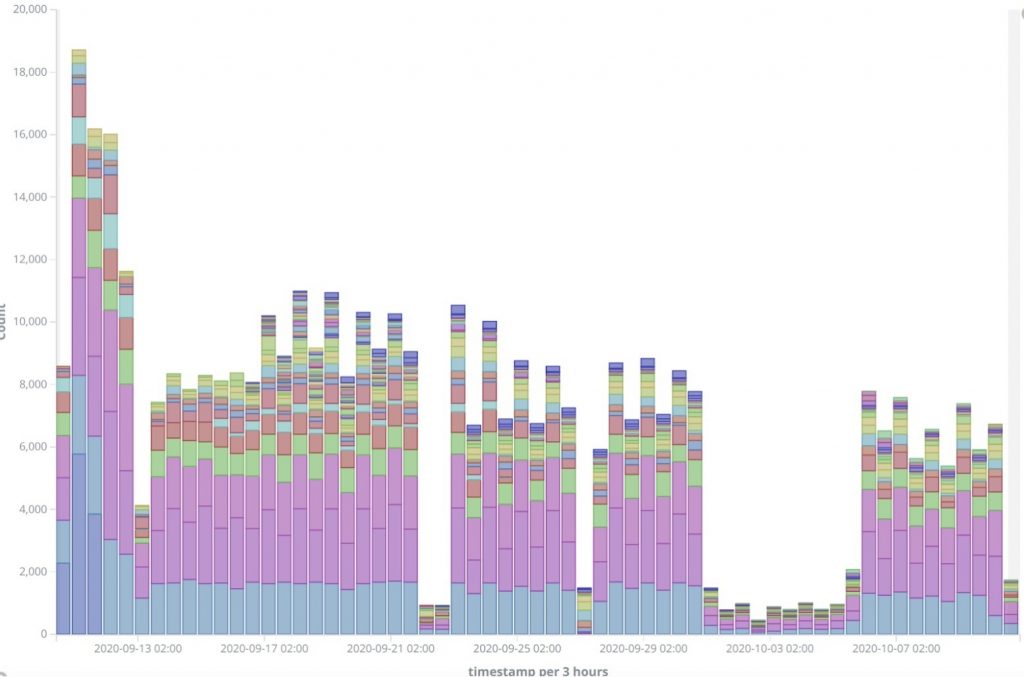
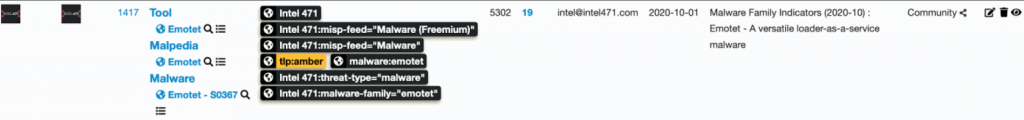
By the Intel 471 Malware Intelligence team. Summary The REvil ransomware-as-a-service (RaaS) operation continues to impact businesses worldwide. The threat actors responsible for developing and maintaining the malware have released an updated ransomware, namely version 2.2. In this short blog post, we will cover the significant changes from the previous version, which we covered in …