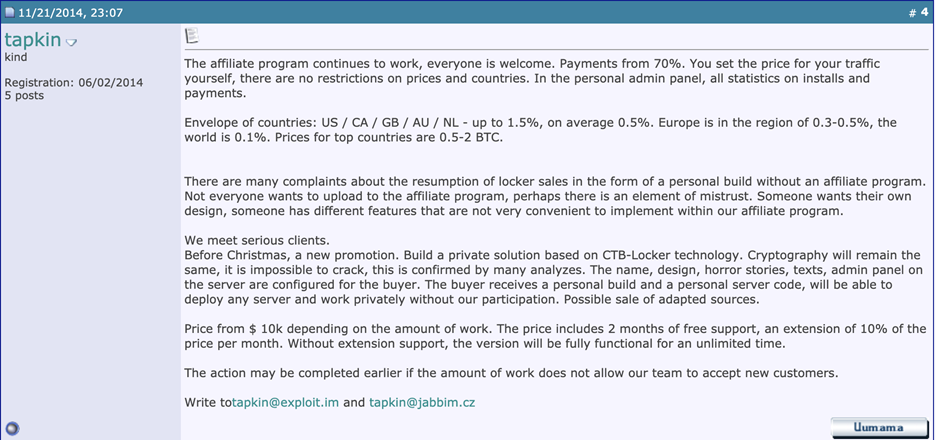
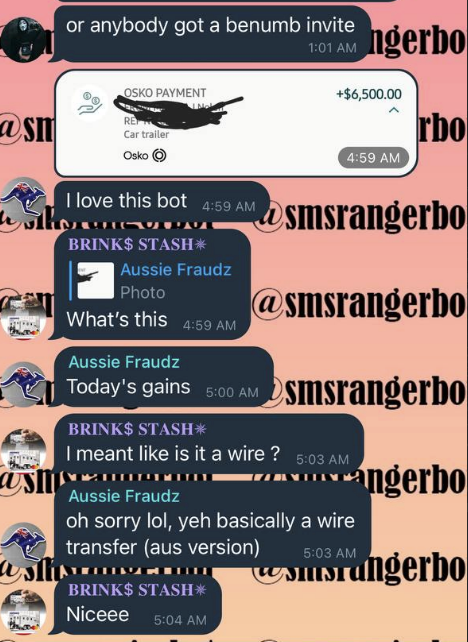
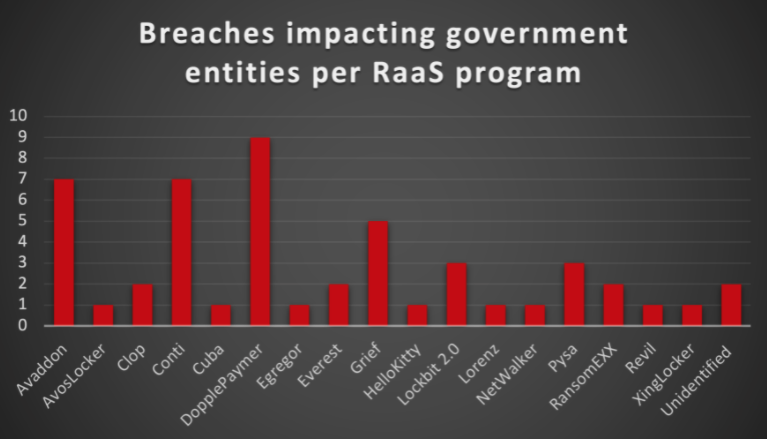
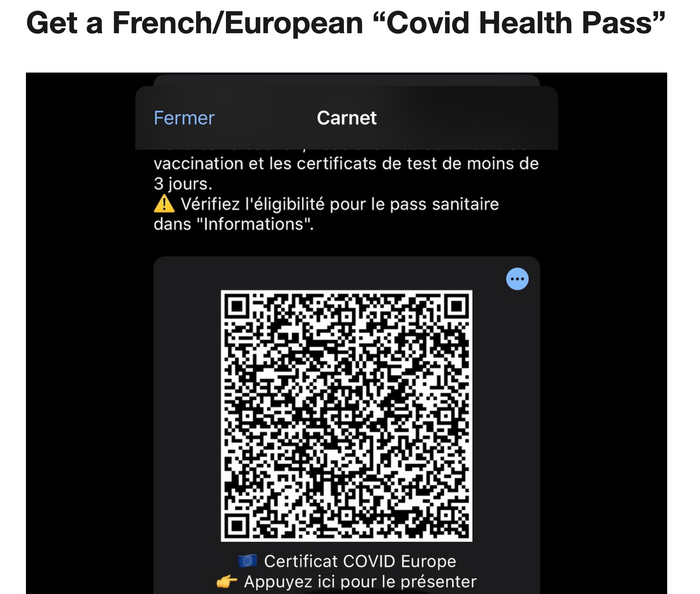
Cybercriminals still leveraging COVID-19 pandemic for…
While the world is starting to see the light at the end of the tunnel when it comes to the coronavirus pandemic, the cybercriminal underground is finding ways to continue its schemes as civil society is trying to repair the wreckage COVID-19 has caused. Intel 471 has observed actors in the underground tailoring their criminal …
Cybercriminals still leveraging COVID-19 pandemic for… Read More »