By Mark Arena, CEO of Intel 471.
This week’s incident with Petya/NotPetya/GoldenEye/Nyetya/Petrwrap has reignited the debate about how security companies name malware. In my opinion, the security industry’s use of different names for the same thing isn’t good for either customers or the industry at large, and it’s something that could be solved without too much effort.
Why do we need consistent naming?
This week I was on a webex with regards to Petya in which there were numerous questions around the naming of the malware. This was clearly confusing for a lot of people who were on the call. When we look into more advanced cyber threat intelligence analysis and tying tools to campaigns and groups, it gets even more complex. An an example, let’s look at “Carbanak”, which is referenced a lot by the security community. The word “Carbanak” is a combination of the words “Carberp” and “Anunak”, which are both trojans/malware used by a variety of different actors and groups. Numerous security companies refer to some malware samples as “Carbanak” and I don’t even know what that means.
What names should we use?
When I think of how we currently name malware, I immediately think of how each language names countries. Let’s look at some examples:
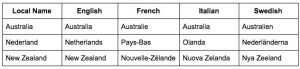
When it comes to naming countries, I’m of the opinion that everyone should call the country by the name the locals call it. And when it comes to malware, I’m of the opinion that we should call the malware the name the bad guys call it — hence my preference for the term Petya. On the (numerous) occasions that we don’t know the name the bad guys call the malware, I’d suggest that the malware be named by the first security company that found it.
An independent and central repository for malware naming
Security companies (Intel 471 included) also need an independent adjudicator to keep us from assigning different names to the same malware. Something like how Mitre handles CVEs could work — just set up a counterpart to “The Standard for Information Security Vulnerability Names”, and call it “The Standard for Information Security Malware Names.”
Ten articles before and after
No, the criminal underground isn’t dropping its use of…
Melting the deep and dark web myth and why we hate the…
Intelligence requirements: Moving from concept to…
Introducing Intel 471’s Cybercrime Underground General…
Malicious actors leverage Coronavirus Disease 2019…
Being a cyber threat intelligence analyst and…
Who hacked the Democratic National Committee?
Cyber threat intelligence: Why should I be worried…