By Michael DeBolt, VP of Intelligence of Intel 471.
Our industry talks a lot about intelligence requirements. Yet I’ve noticed over the years a lack of practical advice being shared about how to actually work with or implement intelligence requirements as a fundamental component of a cyber threat intelligence (CTI) program. In a future blog, I’ll share how we do things at Intel 471, hopefully to help address this gap.
But for now, let’s tackle the disconnect between the concept and practice of intelligence requirements by looking at a few key benefits and challenges.
I’ll go on a limb and predict that most of the CTI industry is totally on board with the concept of intelligence requirements. There is a ton of really great material out there that covers it extremely well (such as this, this, and, of course, that). Thanks to these resources and others, in the last five years our CTI industry has evolved to appreciate the need for intelligence requirements as fundamental to what we do. This is an exciting and positive step that should be celebrated. Now more than ever before, we understand our overall success as intelligence professionals is measured on our ability to satisfy the requirements of our stakeholders consistently and ultimately to inform their decisions and actions that protect our organization.
We know intelligence requirements are important. Here are three key reasons why:
Benefit 1: Maximized resources
Most of us operate in an environment where resources and funding are scarce. A requirements-driven program maximizes our limited time, money and effort by trimming the fat. When done correctly, our human capital and data sources are synchronized, focused and aligned to meet the requirements of our stakeholders. We know exactly what we need to collect, produce, and deliver, and who needs it.
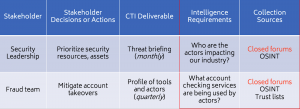
A simplified collection plan showing synchronization between deliverables, sources, stakeholders and intelligence requirements.
Benefit 2: Measured success criteria
There is no ambiguity in what we collect or produce. Each data source, report and deliverable is aimed at satisfying Priority Intelligence Requirements (PIRs) agreed upon by you and your stakeholders. Requirements are frequently revisited with stakeholders to ensure alignment, and any deliverable that regularly falls outside the scope of those requirements requires heavy scrutiny, gap analysis, and justification.
Benefit 3: Demonstrated CTI return on investment
An intelligence program grounded in stakeholder requirements enables objective measurement of intelligence production and impact over time. This helps confidently answer the inevitable question from senior management, “how does our CTI capability provide value to the organization?”
So the concept and justification for requirements is crystal clear and firm — intelligence requirements are the lifeblood of any CTI program.
Ten articles before and after
Introducing Intel 471’s Cybercrime Underground General…
Malicious actors leverage Coronavirus Disease 2019…
Analysis of an attempted attack against Intel 471
REvil Ransomware-as-a-Service: An analysis of a…
Understanding the relationship between Emotet, Ryuk…
Melting the deep and dark web myth and why we hate the…
No, the criminal underground isn’t dropping its use of…
Naming malware: What’s in a name?