By Michael DeBolt, VP of Intelligence of Intel 471.

It’s not deep. It’s not dark. It’s not the ominous underside of an iceberg.
The deep and dark web, or simply the “underground,” as we like to call it at Intel 471, is an organized ecosystem of products, services and goods consisting of real life suppliers and consumers who can be mapped, tracked, understood and exposed.
As an industry, we do ourselves a disservice by often mystifying and overhyping otherwise straightforward concepts, such as the “deep and dark web” for the pursuit of catchy sales pitches or taglines. At first glance, this may seem harmless and nitpicky, but the reality is this sensationalization of the underground causes confusion and disorientation, putting our industry at risk of not being able to fully understand and exploit it for intelligence purposes.
So let’s cut through the jargon and look at four essential characteristics of the underground.
The cybercrime underground is…
Accessible
The popular iceberg metaphor often (and overly) used to illustrate the vastness of the deep and dark web is…., well, flat-out wrong. As Recorded Future correctly points out, the deep and dark web actually is a small fraction of the entire web and it’s not as dark and mysterious as we are led to believe.
So, instead of hyping the “clear, deep and dark” buzzwords, we simply break down the different areas of the web in terms of accessibility and the barrier of entry needed to collect and exploit for intelligence purposes.
Open sources
These resources are any content openly indexed by conventional search engines and publicly accessible via conventional means. In other words, you don’t need specialized software or authorization to access it. Think about open-source news articles, public social media posts and open directories.
Closed sources
This is any nonindexed content gated from public view. Access to closed sources depends on the sensitivity of the underlying content and the privilege needed. Some closed sources require standard username and password access, while others require specialized software and vouches by trusted members of the community. We refer to closed sources where cybercriminals operate as simply the “underground,” which consists of forums, marketplaces, instant messaging platforms, private social media groups and more.
Organized
The “deep and dark web” myth would have you believe it is random and chaotic, but that is not so. In fact, the underground is an organized ecosystem of interdependent suppliers, vendors, consumers, facilitators and active participants. Suppliers offer speciality products and services to prop up the cybercriminal marketplace (i.e., malware, infrastructure and more). These actors use carefully constructed public relations and advertising campaigns to promote their offerings. Any successful supplier worth their weight will carry a positive trackable reputation, while fakers and scammers are identified quickly. These observable aspects of the underground let us lower the noise so we can laser focus our intelligence collection efforts on high-value actors.
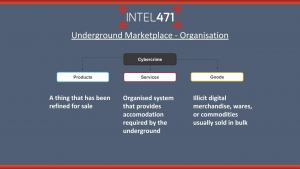
Finite
Unlike the popular belief perpetuated by the “deep and dark web” myth, the underground is a finite space that can be mapped and explained. It consists of hundreds of closed sources, such as forums, marketplaces and instant messaging platforms, where real humans plan attacks, share ideas and do business exchanging data and information. Sure, there are millions of actor handles and indicators in the underground, but only a finite number actually are perpetrating and enabling the majority of cybercriminal activity. Our job as intelligence professionals is to understand how the underground is organized so we can locate, prioritize and collect from the sources and actors that matter.
Exposable
The underground is organized, finite and propped up by real people with natural human instincts and motivations. Our job is to understand these motivations — whether it be financial gain, political cause, or personal fame — and exploit them for intelligence purposes using a combination of automated collection and human engagement. Automation is useful to help sift through and bubble up content. But because we are dealing with the nuances of human behavior in vetted, closed sources, relying solely on a fully automated collection capability will only surface a fraction of intelligence available in the underground. Skilled, native-speaking researchers and sensitive, well-placed sources must be used to gain, maintain and elevate access to top-tier actors to elicit valuable information that only can be obtained through human-to-human interaction.
Don’t believe the hype
As our CEO Mark Arena previously outlined in detail, the cybercriminal underground is available for us as intelligence professionals to map and exploit proactively. Actors operating in this environment are not wearing black hoodies or Guy Fawkes masks. These are real people who have natural tendencies, motivations, reputations and brands, who can be categorized and tiered according to their reputation, history and background. When we intimately understand their business models, processes, enablers and pain points, we are ready to take action to counter the threat proactively.
Ten articles before and after
Intelligence requirements: Moving from concept to…
Introducing Intel 471’s Cybercrime Underground General…
Malicious actors leverage Coronavirus Disease 2019…
Analysis of an attempted attack against Intel 471
REvil Ransomware-as-a-Service: An analysis of a…
No, the criminal underground isn’t dropping its use of…
Naming malware: What’s in a name?
Being a cyber threat intelligence analyst and…