By Michael DeBolt, Vice President of Intelligence.
In the last blog, I outlined three key benefits of a requirements-driven intelligence program. We also looked at three challenges that are preventing many programs from moving from concept to practice.
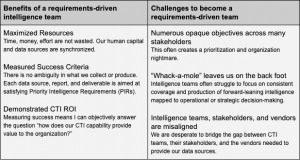
If you didn’t read it, here’s the TL;DR version:
I promised also to share details of how our approach at Intel 471 has helped to empower intelligence teams to tackle these challenges effectively, in the hope that this will assist others to navigate the same journey.
With this in mind, let’s pose the question again… “How to build a requirements-driven intelligence program?”
Adding new tires to existing wheels
As we thought about addressing this challenge at Intel 471, we sought inspiration from existing and proven frameworks and processes.
United States Marine Corps (USMC) “GIR” framework
As a framework, the USMC Intelligence Activity has long used “Generalized Intelligence Requirements (or “GIRs”) to assist human intelligence (HUMINT) collectors in the physical areas they operate. Collectors use a set of prescribed GIRs as a baseline tool to spot and assess collection opportunities against common observables they might encounter in the field.
U.S. Marine Corps GIRs are organized into handbooks for each type of environment Marines typically encounter. For example the UGIRH (PDF) covers commonly asked intelligence requirements when operating in an urban environment. There also is a mountain GIR, and so on.
Could we create a GIR-like framework based on the cybercrime underground?
United States Intelligence Community prioritization process
A framework is great, but without a solid process to apply it against, it becomes useless. Enter the U.S. Intelligence Community’s process for prioritizing requirements across multiple stakeholders. This is a system of collating, weighting, scoring and prioritizing intelligence requirements to produce guidance for collectors and analysts in the field. Every requirement is mapped directly to the stakeholder asking for it. In short, everyone knows what success looks like and how exactly to achieve it.
Could we implement a similar process against a GIR-like framework?
Introducing: Cybercrime Underground General Intelligence Requirements (CU-GIR)
Intel 471’s Cybercrime Underground General Intelligence Requirements (or simply “GIRs”) is a compilation of frequently asked questions or topics based on common observables in the cybercrime underground. Roughly 180 GIRs are organized under a nested tree structure under the following six categories:

GIRs are organization-agnostic
The GIR framework allows for consistent and standing coverage of commonly observed and generalized threats to industry, sector, supply chain and geographic areas of interest, taking advantage of the highly “organized” characteristic of the cybercrime underground, which we outlined in a previous blog.
Conversely, organization-specific intelligence requirements (or “OSIRs”) are custom requirements based on needs unique to an organization or stakeholder. This includes specific infrastructure, technologies, brands, services, and more. We will cover OSIRs in a later blog.
GIRs are mapped to intelligence consumers and use cases
Each GIR maps to typical stakeholders and use cases where cyber threat intelligence (CTI) teams need to produce intelligence. Essentially, GIRs are ready-made intelligence requirements that can be used to bootstrap discussions with your stakeholders.

GIRs are not simple tags
Taking it a step further, each GIR includes a definition and specific essential elements of information (EEIs) that need to be addressed to fulfill or satisfy a particular GIR. As an analyst, these are the questions I will seek to address in my report or deliverable to satisfy a particular stakeholder use case. When content is marked or tagged with a GIR, it means that it fills a gap in knowledge.

For example, GIR 3.1 contains three child GIR entries for the common IaaS types along with the relevant EEIs an analyst needs to address in an intelligence deliverable that satisfies a stakeholder’s use case.
GIRs allow for a range in specificity
GIRs are situated in a nested tree structure to allow for a range in specificity and flexibility in its utility. For example, by addressing the EEIs of a specific child GIR entry, an analyst inherently satisfies the corresponding parent entry.
The graduation of these GIRs across a range of depths, allows organizations to refine their requirements over a period of time to focus on any areas of concern and to address both their specific, granular requirements as well as supporting their broader strategic needs.
How does Intel 471 use the GIR framework?
At Intel 471, CU-GIRs underpin everything we do. GIRs are used as our primary baseline tool to collect, classify and report frequently observed information found in the underground.
Prioritized and focused collection

Customers use our handbook to select and rank subsets of GIRs that are aligned to their stakeholders and use cases. These become client Priority Intelligence Requirements (PIRs). Intel 471 weighs and scores all PIRs and uses the resulting list to prioritize and steer standing collection and production efforts. Using this approach, we also gain insight into priority requirements across industry verticals.
Structured intelligence content and automated routing
Each Intel 471 deliverable is tagged with the applicable GIR or GIRs and automatically highlighted to clients who have matching PIRs.
Measured intelligence production
Synchronizing client PIRs to GIRs gives us a reliable method to measure the value of our intel production against our client needs over time. And, in turn, it gives our clients the ability to objectively measure their support to their own internal stakeholders.
Can other intelligence teams use the GIR framework?
Hopefully it’s clear by now that we want to share the CU-GIR framework with the industry to help empower intelligence teams. We created a handbook called the CU-GIRH, similar to the U.S. Marine Corps UGIRH mentioned previously in this blog, which serves as a baseline tool to assist organizing, prioritizing, producing and measuring production of cybercrime intelligence. Our hope is that it will help for you in whatever stage your CTI program, whether you are bootstrapping a new team or revisiting existing processes.
Still work to be done… and we want your input
At Intel 471, we have seen 1 1/2 years of real-world success by proving the concept of CU-GIRs both internally and with our customers. But this is only the beginning. Like any newly proposed framework or idea, the GIRs is a work in progress. We are eager to see where it goes next.
Currently, a subset of the CU-GIRs are mapped to the top-level of Mitre’s ATT&CK framework. We also are in the early stages of interlacing the CU-GIR framework with FAIR to help inform risk-based decisions and action. We also envision the creation of separate GIR frameworks for coverage of other environments where intelligence collection and production is needed, such as physical security, executive protection, and more. These projects are ongoing and will require feedback and input from the community to get them right.
Ultimately, we are sharing this framework because it provides a practical approach to implement a requirements-driven program, which is a challenge many intelligence teams experience across industry verticals and within both vendor and consumer spaces. Share your thoughts and ideas on this important subject and collaborate with us to further refine the next iteration of the GIR framework. Will GIRs solve all the problems related to intelligence collection and production? No it won’t. But we believe it can help a great deal!
Ten articles before and after
Malicious actors leverage Coronavirus Disease 2019…
Analysis of an attempted attack against Intel 471
REvil Ransomware-as-a-Service: An analysis of a…
Understanding the relationship between Emotet, Ryuk…
COVID-19 pandemic: Through the eyes of a cybercriminal
Intelligence requirements: Moving from concept to…
Melting the deep and dark web myth and why we hate the…
No, the criminal underground isn’t dropping its use of…