Your data security and privacy are our top priorities.
Our pledge to protect your data means that we have several security principles and protocols that we always abide by.
The only information that we come in contact with when you use Shift is your name, email address and general information, such as the location of the device you’re using. To handle even this type of information it is necessary that we adopt practices that maximize security and magnify our efforts in every aspect of our service—and that’s exactly what we’ve done.
In many ways, your data is the lifeblood of your online identity, which is why we take great strides to protect it using a combination of industry-leading data privacy, security, and compliance measures.
We follow one of the most widely regarded and well-respected security protocols in the industry: OAuth 2.0.
What is OAuth?
OAuth is short for open authorization. In the case of OAuth, such authorization is an open standard for access delegation.
So, what does that mean?
Well, in so many words, it means that the OAuth protocol makes it possible for third-party applications (like Shift) and other websites (like Facebook and Instagram) to access your information without touching your password.
Here’s more to help you better understand what all this means…
As an Internet user, it’s both impractical and a security liability to allow every website or application you use to have your password–especially when those entities are designed to serve or host some other third-party resource accounts, like Facebook or Gmail.
This is where OAuth comes in.
As one of the most highly-regarded authentication protocols, OAuth serves as the mechanism that allows websites and applications to access restricted information through what is called an ‘authorization layer.’
The authorization layer requires the client (whatever website or app you’re using) to use an access token to identify your resources, while simultaneously keeping your credentials (as the resource owner) and the actual client completely separate.
The assurance of privacy with OAuth means that your passwords are never exposed, stored, or accessed at any point by the client, whatsoever.
How Does Shift Use OAuth?
Shift uses OAuth exactly as it was intended. To illustrate just how we do this, we’ve listed the process as a series of steps:
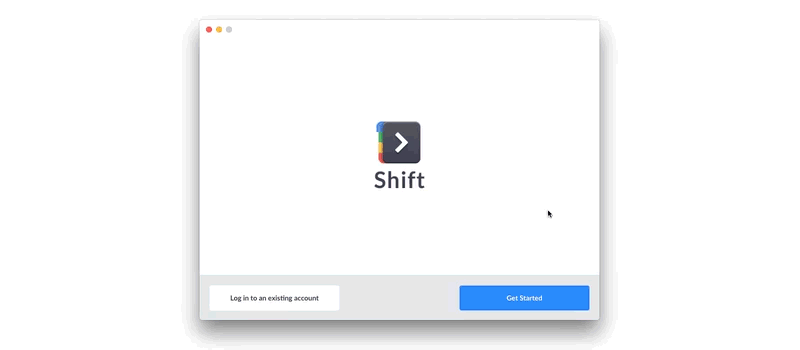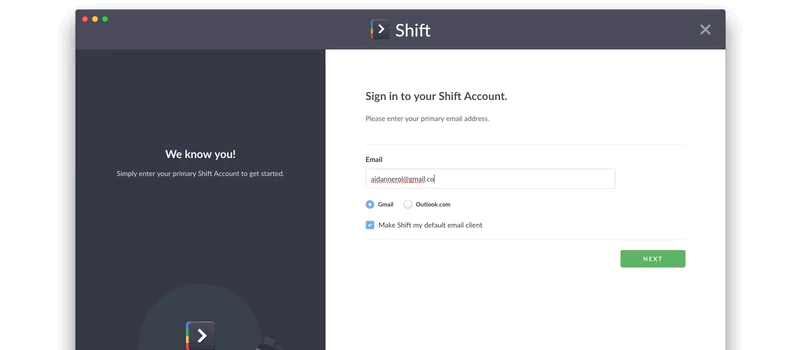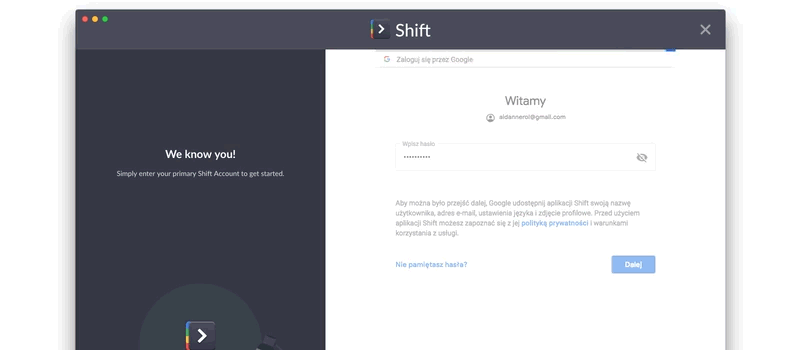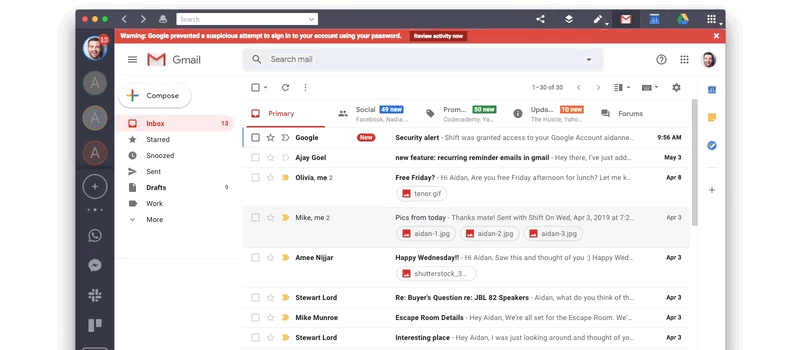
- OAuth captures an authorization token to prove the identity between you and your third-party resource account, in this case, your Gmail / Outlook.com / Office 365 or app accounts.
- Through a delegation protocol, OAuth then provides local authorization to Shift – this allows Shift to display the email account on your computer within the Shift application.
- The identity token that was captured to delegate the authorization layer is stored against your Shift account securely on that service’s servers (in this case, Google or Microsoft).
- The token that was captured to allow Shift access to your emails is stored locally on your computer.
- Shift is given permission to handle and serve your emails locally and privately.
The airtight authentication and delegation processes offered by OAuth guarantee that there is zero risk that anyone—other than yourself—or anything can gain access to your information or emails in any capacity.
Pretty sophisticated, if you ask us.
It’s also important to mention that Shift currently utilizes OAuth 2.0, which is the most recent and secure version of the authorization protocol.
Which Information Do We Collect?
Great question.
We collect a few pieces of data in order to deliver the best service to you, our customers. Specifically, we capture information related to:
- Your user email address (only the actual address, not individual email messages)
- Your IP address
- The version of OS you are using
- Your OS localization
- The version of the Shift application you downloaded
Needless to say, this information is not shared with any third-party entities. Instead, it is used to deliver the best possible service to our customers. Moreover, internally, we use this information to make data-driven product decisions, innovate our feature offerings, and make Shift an all-around stellar product.
And, just to reiterate, we do not collect sensitive information such as your passwords or any log-in credentials. Nor do we have access to your emails–meaning we cannot see them, read them, download them, or otherwise access them.
Conclusion
The security and privacy of our customers’ data are of the utmost importance to us.
In fact, it’s a commitment that guides all of our decision making. Every decision we make is aligned with our values and data security principles. Such decisions include things like continuous monitoring and routine security audits of our applications and server infrastructures.
We consider our relationship with our customers to be our most valuable asset. That being the case, we have adopted set-in-stone protocols for handling and protecting your data.
Again, this is why we entrust only industry-standard measures in the set-up of our data and privacy protocols…and this decision proves best for both Shift and our users every single time.
Ten articles before and after
Tips for Building a Tech Stack for Success
Microsoft Teams vs Slack: Which is Right for Your Team?
How to Use the World’s Most Popular Emojis for Marketing
The Struggles of Managing Multiple Google Profiles (And How to Overcome Them)
The 10 Best Tools for Social Media Management
5 Ways to Practice Mindfulness at Work
How to Design Your Workspace for Maximum Productivity
Top 5 Alternatives to WhatsApp Messenger
Auto-Hibernate: The Feature that Makes a Big Difference to Your Work
Announcing 82 New App Integrations: Apple Mail, Square, and More!